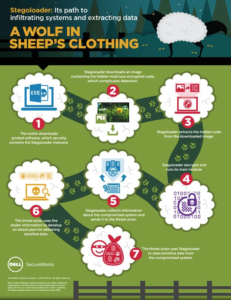
Today, Dell SecureWorks’ Counter Threat Unit (CTU) has released its findings into the little-known malware family called Stegoloader. Appearing to have been active since 2012, this particular malware uses digital steganography – the art of hiding secret information within a digital image or graphic – to conceal its true nature and to avoid detection.
Pierre-Marc Bureau, the senior security researcher leading this project, discovered that Stegoloader operators are hiding a core component of the malware within a portable network graphic (PNG) hosted on a legitimate site. As Stegoloader executes, it downloads the core component and then uses digital steganography to extract the code from the image. The core component is never saved to the victim’s computer, meaning that it is incredibly difficult to detect the malware through regular tools.
So far, the only confirmed distribution channel for the Stegoloader malware is through a software piracy website where it is bundled with key generator programmes; this particular fact might at first suggest that Stegoloader is more of a “mass market” commodity piece of malware than a tool used for targeted attacks. However, operators are only pushing further modules of the malware to computers which they feel are of interest to them – at the moment, systems in the healthcare, education and manufacturing industries have been the most affected by the malware. In fact, if a victim’s system is deemed ‘invaluable’, the Stegoloader actors wipe the malware entirely from the system, proving that these threat actors are selective about the systems they compromise.
The figure below shows Stegoloader’s process. CTU researchers have also published a full analysis of the malware on the Dell SecureWorks website.