The Acunetix annual Web Application Vulnerability Report 2016 has found that high-severity vulnerabilities are on the rise and are now present in the majority of websites globally.
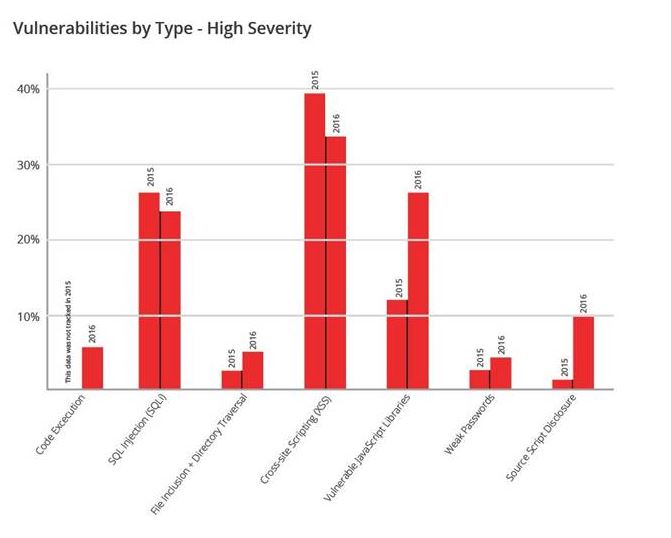
The report looked at 45,000 website and network scans done on 5,700 scan targets from April 2015 to March 2016. Results show that not only do 55% of websites have one or more high-severity vulnerabilities, but this has significantly deteriorated in just one year, growing by 9% over 2015’s report. In addition, 84% of web applications were found to have medium-severity vulnerabilities, while 16% of perimeter network assets were also susceptible to at least one medium severity vulnerability. While this research found a minor, but encouraging reduction in security vulnerabilities such as SQL injection and Cross-site Scripting, these web application vulnerabilities are just two of the top three. The second most prominent vulnerability is Vulnerable JavaScript Libraries (which open up a web app to XSS attacks) – this has shown a significant increase, more than doubling since last year.
On the other hand, Secure Shell (SSH) related vulnerabilities were found to be the most prominent perimeter network vulnerabilities.
Vulnerabilities by type
Organisations are under intense pressure to deliver web apps and web services to meet the demands of modern digital customers. However, app security is not keeping pace with the development cycle, which broadens a brand’s threat surface. Therefore, today there are significantly more flaws for potential cyber attackers to exploit than 12 months ago.
Organisations need to be clear on what this means – a high-severity vulnerability could allow attackers to gain unauthorised access to data and systems, potentially to sensitive financial, customer, health data and trade secrets. They could also move to other systems to escalate the attack even further.
Chris Martin, General Manager at Acunetix, says: “Our research clearly shows high-severity web app flaws are on the rise and older vulnerabilities are still hanging around. Having a plan in place to prioritise these problems – and actually start tackling them – is critical. Using an automated vulnerability scanner such as Acunetix is the first step to protect your brand’s online real estate.”
Download the 2016 Web Application Security Report from: http://www.acunetix.com/acunetix-web-application-vulnerability-report-2016/








