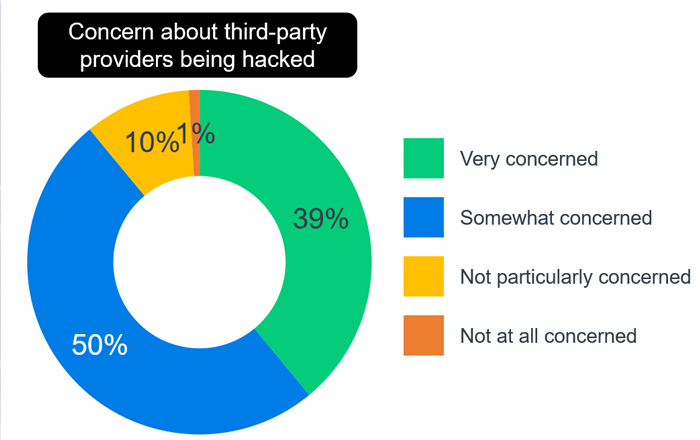
An overwhelming number of cybersecurity professionals (89%) have expressed concerns about the third-party managed service providers (MSPs) they partner with being hacked, according to new research from the Neustar International Security Council.
While most organisations reported working with an average of two to three MSPs, less than a quarter (24%) admitted to feeling very confident in the safety barriers they have in place to prevent third-party contractors from violating security protocols. Along with this concern, security professionals expressed a desire to switch cloud providers, with over half (53%) claiming they would if they could.
These threat levels were also apparent in Neustar’s International Cyber Benchmarks Index, which NISC began mapping trends in 2017, the most recent index revealed an 18-point increase over the two-year period.
Aside from third-party threats, security professionals ranked distributed denial of service (DDoS) attacks as their greatest concern (22%), closely followed by system compromise (20%) and ransomware (19%). Insider threat remained bottom of the list, with 29% seeing it as the least concerning.
In light of continued fears around DDoS attacks, organisations outlined their most recent security focus to be on increasing their ability to respond to DDoS threats, with 57% admitting to having been on the receiving end of an attack in the past. In the most recent data set collected and analysed by NISC, enterprises were most likely to take between 60 seconds and 5 minutes to initiate DDoS mitigation.
“Regardless of size or sector, every organisation relies on third-party service providers to support and enable their digital transformation efforts. Whether it’s a business intelligence tool, cloud platform or automation solution, the number of MSPs businesses work with is only set to increase, as enterprises continue to chase agility and find new ways to attract customers,” said Rodney Joffe, Chairman of NISC, Senior Vice President, Security CTO and Fellow at Neustar. “However, by multiplying the number of digital links to an organisation, you also increase the potential for risk, with malicious actors finding alternative ways to infiltrate your networks.”
“While businesses should adopt their own, always-on approach to security, it’s essential that they are also questioning the security of their whole digital network, including the third parties they work with. Missed connections or weak links can cause lasting damage to an organisation’s bottom line, leaving no room for error,” Joffe added.
Methodology
Survey participants in July 2019 comprise 314 professionals from across six EMEA and US markets. All are in senior positions within their organisations and able to provide informed opinions about cybersecurity issues, including how these are impacting their enterprise and the wider business community.