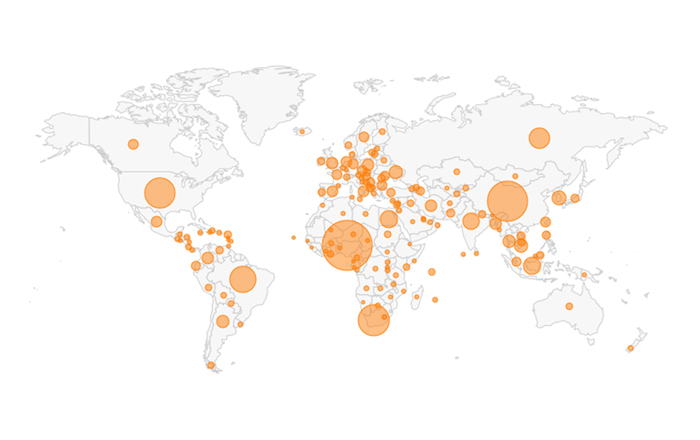
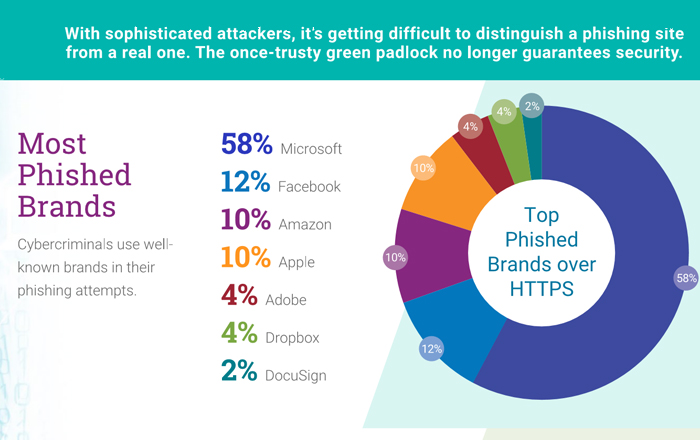
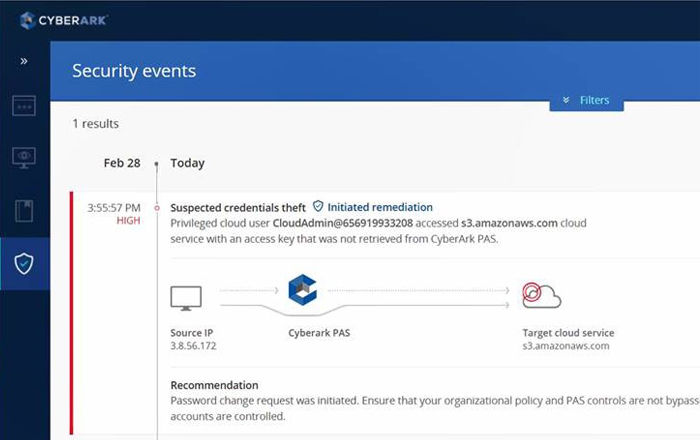
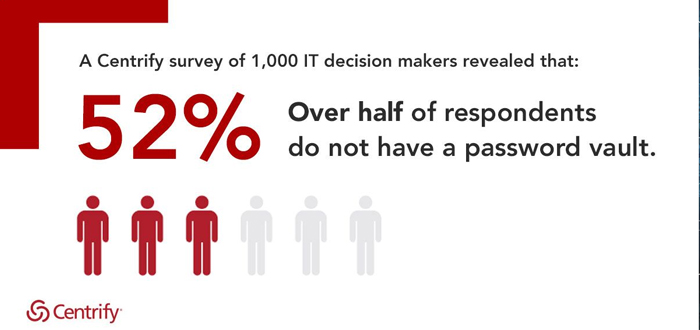
Proofpoint, Inc., a leading cybersecurity and compliance company, today released its Cloud Application Attack Snapshot: Q1 2019 research, which examined over one hundred thousand cloud application attacks aimed at global organizations between September 2018 and February 2019. Overall, targeting attempts increased by 65 percent during that time period with 40 percent originating in Nigeria. China was the second most prevalent country of origin, with 26 percent of attacks originating from Chinese IP addresses. Cloud application...
Read more