Tesla Motors’ website was “hacked” on Saturday as well as its official Twitter account. The teslamotors.com website was redirected to a server hosted in Amsterdam and within a few minutes, the account began sending tweets promising free Tesla cars. Later that same day it was revealed that Tesla founder Elon Musk’s Twitter account was compromised. According to Dave Smith at Business Insider “though the parties claiming responsibility offer up different names, it appears to be one coordinated attack on all of Musk’s online and social properties.”
Andrew Hay, director of research at the OpenDNS Security Labs team has laid out the process that attackers used to hijack Elon Musk’s personal Twitter account, as well as the Tesla Motors website. It gives a deep dive on the infrastructure used in the attack.
1) This was not a “hack,” but a series of related defacements
We’d first like to communicate that we believe this to be a compromise, and not necessarily a “hack.” This attack (and we use the term loosely) involved the redirecting of legitimate traffic destined for teslamotors.com to an IP address of the attackers’ choosing.
Visitors to the domain were presented with the following page (as captured by David Maynor via his Twitter feed)
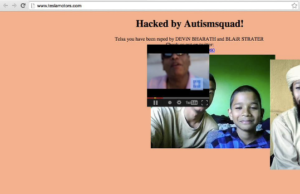
At roughly the same time, the corporate Twitter account for Tesla was compromised. Once controlled by the attackers, several tweets appeared from the @TeslaMotors Twitter account and the name of the account was changed to “#RIPPRGANG.” The account also tweeted the number to call to get a free Tesla. The number was that of a small computer repair shop in Illinois. Elon Musk’s account also began tweeting messages about free cars and where they can be picked up–at the same address in Illinois.
2) The domain registrar may have been socially engineered to give up control of the teslamotors.com domain
It appears that very little sophistication was involved in this defacement. As such, there was initial speculation of a social engineering (SE) attack against the domain registrar but sources close to the investigation inform us that the SE attack vector was not exploited.
A SE attack against the registrar would explain how the attackers were able to gain access to both the corporate Twitter account and the account of founder Elon Musk. By controlling the domain, and by association the MX (mail exchange) records, the attackers could request a password reset for the Twitter accounts.
By controlling the MX record, the e-mailed password resets would have given the attacker control of the social account passwords.
The official statement from Tesla, as told to Thomas Fox-Brewster of Forbes, was that
“Posing as a Tesla employee, somebody called AT&T customer support and had them forward calls to an illegitimate phone number. The impostor then contacted the domain registrar company that hosts teslamotors.com, Network Solutions. Using the forwarded number, the imposter added a bogus email address to the Tesla domain admin account. The impostor then reset the password of the domain admin account, routed most of the website traffic to a spoof website and temporarily gained access to Tesla’s and Elon’s Twitter accounts.”
Tesla’s corporate network, cars, and customer database were not affected and everything has been restored to normal, according to the spokesperson.
“We are working with AT&T, Network Solutions, and federal authorities to further investigate and take all necessary actions to make sure this never happens again,” the spokesperson added.
So the domain registrar was not SEd, but rather AT&T. This is not the first time that AT&T was tricked into redirecting calls to an illegitimate phone number.
3) DNS shows a timeline of changes during the attack
OpenDNS’ investigated results for teslamotors.com, the domain’s IP address was changed on April 25th from 205.234.27.220 to 4 additional IP addresses not owned or controlled by Tesla.
4) So far, nothing indicates visitors were at risk for malware downloads. The teslamotors.com domain received a surge in visits between 04:00 and 07:00 UTC. The most significant spike to the domain occurred on April 26th at 05:00 UTC. This was likely due to the attackers publicizing the “hack.” The subsequent Internet frenzy to visit the site ensued and was noticed by more than a few individuals.
There is no indication of any malware being dropped, nor were visitors redirected to another site to download malware. This can be verified by the HTML dump of the fraudulent site on Pastebin: http://pastebin.com/j6kz0Kdk.
5) The Islamic State of Iraq and ash-Sham (ISIS) was not likely involved, but Lizard Squad may have been?
At one point during the campaign, the teslamotors.com site was redirected to another fear-inspiring domain: isis[.]camp.
Now http://t.co/Y0Ab1JRkjM points to a domain with ISIS in it. #tesla#hackpic.twitter.com/LHItCZcJbT
The newly created domain was registered at ENom and hosted at DreamHost Web Hosting for a brief time.
So was this the work of ISIS? In a word, unlikely. It’s incredibly unlikely that ISIS would have it out for Tesla as a company. It’s even more unlikely that they’d direct their anger at a small Illinois-based computer repair shop. There are speculations around the research community, as well as the targeted individual, that this breach was the work of “Ryan” aka “zeekill” aka “Julius Kivimäki”, a Finish national with alleged ties to Lizard Squad.
Receiving reports that Julius Kivimaki hacked Tesla and Elon Musk’s Twitter accounts and websites by Social engineering NetworkSolutions
— r000t (@rootworx) April 26, 2015
OpenDNS can neither confirm nor deny attribution at this time.
The use of Jihadist-inspired defacements is not new. As many of these defacements are meant to drive traffic to the hijacked site, instill fear, and increase publication int he popular media, the use of controversial (yet unrelated) imagery and messaging is becoming common place.
As always, please let us know if you have any additional information or would like to talk to us about our findings.
See more at: https://labs.opendns.com/2015/04/27/five-things-to-know-about-the-tesla-motors-compromise/#sthash.PbStdcJh.dpuf








