Imagine if an authoritarian state had a tool to get private information about users visiting certain websites, including real names, cookies, mail addresses, sex, birthdays, phone numbers, etc. Imagine that even users that run TOR or VPN connections to bypass the tools that the authoritarian government uses to block and monitor these websites were exposed to this technique.
A new research paper has been published, revealing how Chinese hackers have exploited vulnerabilities in the country’s most frequented websites to target individuals accessing web content that state censors have deemed hostile.
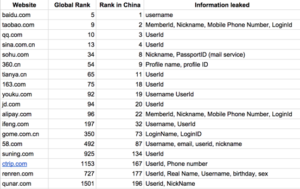
The research, by Jaime Blasco, Vice President and Chief Scientist at AlienVault, details a new watering hole attack being used to identify and track users in China who visit websites that are blocked by the China’s censorship technology, often called the Great Firewall. The attacks exploit vulnerabilities in the top 5 websites used in China, including those run by Baidu and Alibaba, and use cross-site request forgery to expose users even if they have been accessing restricted sites via the TOR or VPN – two of the most trusted privacy tools on the internet.
The vulnerability, known as JSONP, was first publicised in 2013, but the affected sites did not patch the problem, making these most recent attacks possible. The paper outlines how affected sites can fix JSONP hijacking vulnerabilities. It also warns private web users who live in an authoritarian country or are worried about being tracked to follow best practices when browsing the web, such as not browsing sensitive websites while logged into another website – even in a different tab or window.
To describe the severity of the issue, we are showing a list of Alexa ratings for the affected services and the personal data the attackers are able to steal: