The Great Cyber Comparison: Anthropology of Modern Malware and Development of Civilizations
Cyber Global Warming (6 Steps Towards Meltdown)
Brian Laing, Lastline
I began attending the RSA security conference in the late 1990’s. Back then the show had only a few thousand attendees and security companies were lucky to see a couple of public breaches in the news each year. Not only that, but you could count the companies focused solely on security on two hands – How times have changed! Now there are hundreds of security companies and this year’s RSA attendance hit a record 33,000 people. The show filled not just one side of San Francisco’s Moscone Center, but both sides– a feat few other shows have been able to do.
A lot has changed in the security space over the last ten to fifteen years. I know that seems like a long time, but the Internet is changing so rapidly that we do not yet even fully understand all the ramifications that these changes bring. In John McWhorter’s TED2013 talk: Txtng is killing language. JK!!!, he states that, “if humanity had existed for 24 hours, then writing only came along at about 11:07 p.m.” If we were to include the Internet in that analogy we would be looking at 11:59 PM with some small fraction of seconds Left in the day.
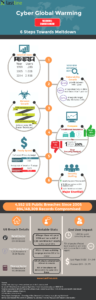
These changes are very similar to the factors covered In, Guns Germs and Steal. Jared Diamond covers a chain of causation leading up to proximate factors (guns, horses, diseases, etc.), which drove the overall growth in civilization. The six steps outlined in my infographic plot a similar chain of causation for cyber security: Internet users, quantity of vulnerabilities, increase in malware, lack of effective security, lack of security budgets and finally, the lack of adequate security staff. This cyber security chain of causation has led to the proximate factors of weaponized malware, data theft, and an escalating digital arms race. Making it possible for attackers to move from indiscriminate untargeted attacks to structured targeted attacks delivering huge financial gains!
Step 1. Population growth in Internet users is the leading motivator of the exponential growth in security issues. In 1997, this 6th edition Internet Yellow pages had “Site descriptions and links to 10,000 sites”. In 1999, the number of Internet users was 280 million. By 2005, this number had grown to just over one billion and by 2014 there were almost three billion! This explosive growth in users went hand-in-hand with the growth of websites and countless new services looking to hop on the Internet bandwagon, including search engines such as Yahoo and Google.

Step 2. Along with the growth in Internet users, there has been a huge increase in the number of vulnerabilities (a bug or weakness in software that can allow attackers to access to your information and steal your data). In the nascent days of security, vulnerabilities were not even tracked. Instead we related to them based on the interesting names given we gave them, like “OOB” and “Son of OOB”. As more vulnerabilities were found and exploited, they were given numbers and tracked through the Common Vulnerability Exchange (CVE) at Mitre. According to those CVE stats, since 1999 the number of vulnerabilities has grown by 510%. Many of those required a software update to be patched — a slow and difficult process. And considering the large number of machines needing a patch, this is certainly a daunting task! Like most unpleasant tasks, the patching of machines is often deferred, leaving who knows how many machines open to attack. Attackers aren’t being clever when they target old vulnerabilities today; they’re being practical. 99% of the exploited CVE in 2014 were more than a year old! Attackers are saving their zero days (vulnerabilities that are not public) for special targeted attacks or for selling on the blackmarket.
Step 3. In previous entries I talked about how initial virus infections spread via floppies. While malware capabilities have increased, so have their sheer numbers. Let me take you back again to the late 1990’s. There were a number of incidents when I found a file infected with a new virus. I actually walked down the block to McAfee, presented them with the file and chatted while they gave me a new build of their software to clean it. Of course, that was then and this is now. The numbers of new malware today make that process impossible. In fact, I don’t think many would disagree that signature-based AV is long dead! Avtest.org keeps track of the amount of new malware each year. In 2005, there were 333K new pieces of malware. By 2014, this number had grown to 392K pieces of new malware PER DAY! And today’s malware is much more aggressive and deadly. In 2014, Lastline detected malware that combined to use over 500 different evasion techniques! Stay tuned for the weaponization of malware in my next blog segment.
Step 4. Almost everyone has some form of insurance: house, automotive, life, medical, etc. These types of coverage all have one thing in common that security budgets do not – they are 100% effective. As an insurance holder, you pay a premium and (within the limits of your policy) you are covered. Most companies have a multi-layered security plan with budget set aside for a number of different products, services and staffing. While insurance is paid in case there is an issue, the security spend is prophylactic against a breach. Based on the average security budget and the cost of a breach, handling one single breach will cost the targeted company an additional 200% of what they already spent on security.
Step 5. Not only is the cost of a breach out of sync with what is spent on security, we have a similar disparity with the overall IT budget. There is a huge chasm between what is spent on traditional IT and Security. Of the overall IT budget, 96.34% is spent on traditional IT, with just 3.66% spent on security.hat is not a typo—3.66%! And the numbers flip when we contrast how much an IT outage costs compared to a security breach. The average breach will cost $8.2M in lost revenue and additional costs.An IT outage? Only $627K. So here’s the obvious question – why aren’t we spending more on security?
Step 6. The massive adoption of the Internet has required whole new skills sets in IT, networking and security. Unlike other fields that have had decades to mature, these roles have grown so quickly that there has not been time for the market to adapt. I bet you can guess which one has suffered the most – Yes, security. Job postings in the security space have grown 74% since 2007. In 2014 alone, 50,000 new job postings required the applicant to have a CISSP certification. There are currently only 60,000 CISSP holders available, most of whom aren’t looking for a new job! Complicating the issue further are hiring managers who lack the understanding to properly vet applicants.
Security is currently in a state of near meltdown. Just Google the Sony or Target breaches – anyone can see the impact. The Target breach was not some new cutting-edge attack. Target even had a product deployed that detected the attack. Had the product been configured properly it may have stopped the leak of 40M credit cards, but the ALARM went unnoticed! Qualified security employees are a fledgling species. Since 2005 there have been 4,552 public breaches in the US with 994,148,309 (yes, almost a billion) records being compromised! With adequate resources, it’s anyone’s guess how many of those could have been prevented. Rather than stabilizing, the problem is accelerating. The billion-dollar question is how do we adjust priorities and budgets, and encourage people to get educated in cyber security? Something has to change if we have any hopes of reversing the trend!
Brian Laing is an executive at IT security innovator Lastline. An entrepreneur and on the frontline of the security industry for more than 20 years, Brian is a leader in strategic business vision and technical leadership, shown through his work with a range of start-ups and established companies. Brian founded RedSeal Networks as well as Blade software, who released the industry’s first commercial IPS/FW testing tools.
Brian Laing is an executive at IT security innovator Lastline. An entrepreneur and on the frontline of the security industry for more than 20 years, Brian is a leader in strategic business vision and technical leadership, shown through his work with a range of start-ups and established companies. Brian founded RedSeal Networks as well as Blade software, who released the industry’s first commercial IPS/FW testing tools.
Twitter @brianlaing
https://www.linkedin.com/in/blaing








