According to recent research[1] from Kaspersky Lab and B2B International, nearly half (45 per cent) of all businesses recognise the serious threat posed by cryptomalware, also known as ransomware, – a sharp increase from 37 per cent in 2014. However, despite this rising awareness, cryptomalware attacks continue to severely impact companies, with the CryptoLocker ransomware, for example, believed to have infected more than 234,000 computers worldwide.
The global cyber-threat landscape continues to expand and cyber-criminals have discovered that the malicious encryption of data, followed by a ransom demand, can be highly profitable. Many companies admit that they often just pay up. The gang behind CryptoLocker is believed to have made $30 million in the space of just 100 days, while the creators of CryptoWall may have pocketed as much as $325 million.
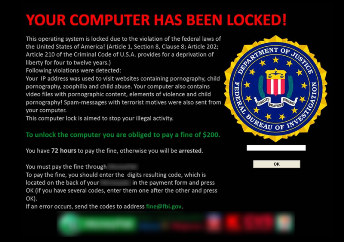
Businesses are a tempting target for ransom attack. It doesn’t matter if they are very small or of enterprise size, cryptomalware will find a way in if there is no security to block it. Like other forms of malware, it enters a network through emails, malicious attachments or links from a compromised website, which is then opened, downloaded or clicked on by unsuspecting employees. There are no signs to alert a user that they have been infected until they receive the ransom demand.
A reliable, multi-layered security solution is the only thing that will stop cryptomalware in its tracks.
“Cryptomalware attacks are profitable and increasingly popular with cyber-criminals. Businesses often pay up without realising that there is no guarantee that their data will be unlocked when they do – and there is new evidence that poorly-coded ransomware can mean some information is never recovered. The best way to protect the company’s data and assets is to implement comprehensive cyber-security measures that cover everything from infrastructure and storage to mobile networks – all accompanied by employee awareness and education. Furthermore it’s essential that data is backed up regularly, so that the company doesn’t find itself in the invidious position of having to choose between paying the ransom or losing data,” said David Emm, Principal Security Researcher, Kaspersky Lab.
To help companies, regardless of the size, address the growing threat of cryptomalware and protect all of their IT assets and infrastructure, Kaspersky Endpoint Security for Business and Kaspersky Small Office Security provide reliable protection against known, unknown and advanced cyber-threats, including ransomware attacks.
The solution includes Kaspersky Lab’s System Watcher module, designed to keep local, protected copies of files and revert any changes made by cryptomalware. By scanning the most relevant system event data it can track information about the creation and modification of files and identify any changes to the system and data transfers over the network. By independently making decisions about whether a program is malicious, it can deliver better overall detection of ransomware and security policy breaches for comprehensive protection. The module also enables automated remediation and saves time and effort associated with restoring data from backups and the impact of downtime.
[1] The information security of businesses – Kaspersky Lab and B2B International, 2015. Over 5,500 IT specialists were surveyed from more than 25 countries around the world.