The tools used by cyber-criminals against businesses in 2015 were different to those used against consumers, according to Kaspersky Lab’s review of corporate threats in the last twelve months. They included greater exploitation of legitimate software programs and malware being signed with valid digital signatures to keep malicious files hidden for longer. Kaspersky Lab’s experts also observed a steady rise in the number of corporate users attacked by ransomware.
Kaspersky Lab’s experts found that in 2015 well over half (58 per cent) of corporate PCs were hit with at least one attempted malware infection, up three percentage points on 2014. One in three (29 per cent) business computers were exposed at least once to an Internet-based attack; with the exploitation of standard office applications seen three times as often as in consumer attacks.
Geography of online attacks
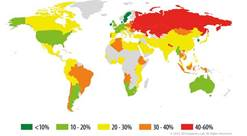
Percentage of attacked corporate users in each country
Further, 41 per cent of business computers faced local threats, such as from infected USB sticks or other compromised removable media. The experts also noted a seven per cent increase in the share of exploits targeting the Android platform, confirming hackers’ growing interest in data stored on employees’ mobile devices.
These attacks were found to be carefully planned, with cyber-criminals taking time to investigate a target company’s contacts and suppliers and even the personal interests and browsing habits of individual employees. This insight was then used to identify legitimate websites for compromise and malware distribution, with the attacks often repeated over time.
Hunting down the money
In 2015, cyber-criminals and advanced persistent threats (APT) groups focused a great deal of attention on financial services organisations, such as banks, investment funds, and both stock and currency exchanges, including those handling cryptocurrencies.
These attacks included Carbanak, which penetrated the networks of banks, seeking out critical systems that would allow it to withdraw money. One successful attack alone would bring in as much as £1.6 – £6.6 million. The cyber-espionage group, Wild Neutron also spent much of 2015 hunting down investment companies as well as organisations working with the cryptocurrency Bitcoin and companies involved in mergers and acquisitions.
Diversification
Kaspersky Lab’s experts observed a growing diversification in attack targets. For example, in 2015, the Chinese APT, Winnti APT switched targets from companies involved in computer games to those in pharmaceuticals and telecommunications.
“The future cyber-landscape for business includes a new attack vector: infrastructure, because almost all of an organisation’s valuable data is stored on servers in data centers. We also expect tougher safety standards from regulators, which could lead to more cyber-criminals being arrested in 2016,”- says Yury Namestnikov, Senior Security Researcher at Global Research and Analysis Team, Kaspersky Lab.
Stealing at point of sale
Point-Of-Sale terminals, used by retailers and other consumer-facing organisations were another target for attack in 2015, with Kaspersky Lab products blocking more than 11,500 attempts to hack into PoS devices. The company knows of ten families of programs designed to steal data from PoS terminals, and seven of them appeared for the first time this year.
The rise and rise of ransomware
2015 also saw a doubling of the number of cryptolocker attacks, with Kaspersky Lab detecting cryptolockers on more than 50 thousand corporate machines. This could reflect the fact that ransoms received from organisations can be far larger than those received from individuals. There is also a greater likelihood of the ransom being paid. Many companies simply cannot function if the information on several critical computers or servers is encrypted and inaccessible.
“Organisations that have fallen victim to a cryptolocker can find themselves faced with a ransom demand to stop a DDoS-attack, decrypt files, or maintain the confidentiality of any stolen information. Because the evidence shows that cyber-criminals don’t always honor the agreement once the ransom has been paid – as happened in the case of the DDoS-attacks on Proton-mail, many of those affected should call in law enforcement and computer security experts, “- says Yury Namestnikov, Senior Security Researcher at Global Research and Analysis Team, Kaspersky Lab.
Kaspersky Lab recommends that companies take steps to reduce risk and to increase their knowledge of the latest threats. The basic principles of security in corporate networks remain the same: train employees, establish robust security processes and make full use of new technologies and techniques as each additional layer of protection reduces the risk of network penetration.
To eliminate the threat of ransomware infection, companies should use protection against exploits and ensure that their security solutions include behavioral detection methods, such as Kaspersky Lab’s System Watcher.