Kaspersky Lab’s Global Research and Analysis Team has announced the discovery of the Poseidon Group, an advanced threat actor active in global cyber-espionage operations since at least 2005. What makes the Poseidon Group stand out is that it’s a commercial entity, whose attacks involve custom malware digitally signed with rogue certificates deployed to steal sensitive data from victims to coerce them into a business relationship. In addition, the malware is designed to function specifically on English and Brazilian Portuguese Windows machines, a first for a targeted attack.
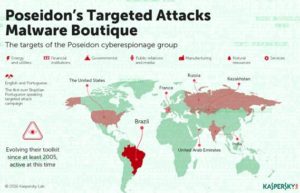
At least 35 victim companies have been identified with primary targets including financial and government institutions, telecommunications, manufacturing, energy and other service utility companies, as well as media and public relations firms. Kaspersky Lab experts have also detected attacks on service companies that cater to top corporate executives. Victims of this group have been found in the following countries:
- United States
- France
- Kazakhstan
- United Arab Emirates
- India
- Russia
However, the victim spread is heavily skewed towards Brazil, where many of the victims have joint ventures or partner operations.
One of the characteristics of the Poseidon Group is an active exploration of domain-based corporate networks. According to Kaspersky Lab’s analysis report, the Poseidon Group relies on spear-phishing e-mails with RTF/DOC files, usually with a human resources lure, that drop a malicious binary into the target’s system when clicked on. Another key finding is the presence of Brazilian-Portuguese language strings. The Group’s preference for Portuguese systems, as revealed by the samples, is a practice that has not previously been seen.
Once a computer is infected, the malware reports to the command and control servers before beginning a complex phase of lateral movement. This phase will often leverage a specialised tool that automatically and aggressively collects a wide array of information including credentials, group management policies, and even system logs to better hone further attacks and assure execution of the malware. By doing this, the attackers actually know what applications and commands they can use without alerting the network administrator during lateral movement and exfiltration.
The information gathered is then leveraged by a fronting business to manipulate victim companies into contracting the Poseidon Group as a security consultant under the threat of exploiting the stolen information in a series of shady business deals to benefit Poseidon.
“The Poseidon Group is a long-standing team operating on all domains: land, air and sea. Some of its command and control centers have been found inside ISPs providing Internet service to ships at sea, wireless connections as well as those inside traditional carriers,” said Dmitry Bestuzhev, Director, Global Research and Analysis Team, Kaspersky Lab Latin America. “In addition, several of its implants were found to have a very short life span which contributed to this Group being able to operate for such a long time without being detected.”
As the Poseidon Group has been active for at least ten years, the techniques used to design its implants have evolved, making it hard for many researchers to correlate indicators and put all of the pieces together. However, by carefully collecting all the evidence, working with the threat actor’s calligraphy and reconstructing the attacker’s timeline, Kaspersky Lab experts were able to establish by the middle of 2015 that previously detected but unidentified traces in fact belonged to the same threat actor, the Poseidon Group.
Kaspersky Lab’s products detect and remove all known versions of Poseidon Group components.
To read the full report on the Poseidon Group with a detailed description of the malicious tools and stats, together with indicators of compromise, see Securelist.com
Learn how sophisticated targeted attacks are investigated: http://www.youtube.com/watch?v=FzPYGRO9LsA
More about cyberespionage operations here: https://apt.securelist.com/








