Cyber security firm Imperva has released a new behind-the-scenes report into the infamous CryptoWall 3.0 ransomware, which show just how much cybercrime pays.
CryptoWall is one of the most dangerous pieces of ransomware around today and it is estimated to have resulted in $325 million in damages.
While many reports and research publications go into great detail explaining the anatomy of different ransomware malware. Imperva’s report clearly demonstrates that peeling the layers behind the financial infrastructure of ransomware is achievable and such investigations could be a powerful tool if undertaken by the appropriate authorities. Imperva believes one of the reasons ransomware is thriving is the lack of action from law enforcement agencies.
Key findings from the report:
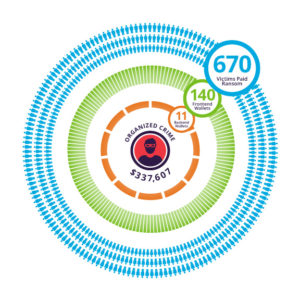
- Imperva’s new report analyses the Bitcoin Wallets used by a small organised cybercrime ring behind CryptoWall 3.0 and traces how they were able to collect more than $330,607 in ransom from some 670 victims.
- Another interesting fact which is revealed in the report is that the ransomware advertises a different fee depending on the geographical location of the victim. Interestingly, the ransom amount for the USA is $700 USD whereas for Israel, Russia, and Mexico, it’s only $500 USD. This clearly shows malware authors understand average incomes and change ransom demands based on geolocation to keep the payments affordable.
- From the study Imperva was able to identify ~1217 BTC ($337,607 USD) being paid out in ransom in a short period. However, it is likely that with more in-depth sibling analysis, more wallets can be identified, in addition to this, because the results are from an ongoing campaign the payments will likely rise.
Commenting on the research, Mark James, security specialist at ESET, said: “Cryptowall or indeed any ransomware malware poses a very real threat to many computer users because of the potential damage to files that so many still fail to backup. Considering this is something that is so simple to defend against, it is still so widely used and often successfully. The fact that it will adapt for the market area it is infecting shows that the malware writers do have an understanding of how important it is to tailor the ransom in an affordable way to ensure the biggest hit rate in gaining funds. “








