ESET® warns users against an increased number of infected emails containing a malicious attachment, which downloads and installs ransomware onto an infected device. When opened, it encrypts victims‘ files on thier PCs and requires a ransom for decryption.
ESET telemetry detects this malicious downloader as JS/TrojanDownloader.Nemucod and records its unusually high incidence in Europe, North America, Australia and Japan.
Nemucod is wide-spread via emails, which contain attached zipped files. Emails are written in a very trustworthy way, claiming to be invoices, notices of appearance in court or other official documents. Attackers are just trying to get users to open the malicious attachment that contains a JavaScript file, which after it is opened, donwloads and installs Nemucod to the victims PC. Nemucod is known for downloading a diverstiy of other malware available in-the-wild.
„Nemucod currently downloads mainly ransomware, for example TeslaCrypt or Locky. These encrypt the data on the victim‘s computer and demand ransom,“ says Peter Stančík, Security Evangelist at ESET.
Both TeslaCrypt and Locky ransomware use encryption standards similar to those used by financial institutions when securing online payments.
Commenting on this sudden surge of ransomware emails, David Gibson, VP of strategy and market development at Varonis, said, “Ransomware attacks grow more common because they’re effective and lucrative. They’re effective because it’s relatively easy to trick someone into downloading malware via phishing , and once a user launches a piece of ransomware it often won’t be detected (until it’s too late) because most aren’t watching or analysing file activity on networked file shares or in SharePoint. This means that it’s difficult to spot and stop an attack/infection while it’s in progress. Without a record of activity, it’s difficult to know which files were encrypted and when, so recovering from backup can be challenging. It’s lucrative because many people and organizations end up deciding it’s just easier to pay. User Behaviour Analytics that incorporates file activity can help detect and stop the spread of malware, and make recovery much more straight-forward.”
How to protect against this threat:
- Do not open attachments sent to you in emails from unknown senders.
- Warn colleagues who most frequently receive emails from external sources – for instance financial departments or human resources.
- Regularly backup your data. In case of infection, this will help you recover all your data. An external disc or other storage should not remain connected to computer in order to avoid infection by filecoder.
- Regularly install updates of your OS and other software you use. If you still use Windows XP, seriously consider moving to other, supported operating system of Windows.
- Security software must also be used with all updates installed, ideally with the latest version. IT security vendors are packing new versions of their software with additional scurity features.
- Users of ESET solutions are protected when ESET LiveGrid® Reputation System is turned on. This technology protects users‘ devices against ransomware by actively blocking their processes.
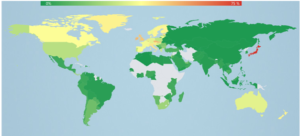
Prevalence level of the Nemucod malware. The scale spans from 0% (deep green) to 75% (Japan).
Source: http://virusradar.com/en/JS_TrojanDownloader.Nemucod/map
Fraser Kyne, principal systems engineer at endpoint security firm, Bromium, added “Ransomware is a particularly nasty form of malware because, once you are hit with its encryption, your files are toast. Anti-virus can’t do anything to bring those encrypted files back to you. I only expect this trend to continue because it is so effective, and this increase in ransomware highlights the importance of best practices, such as endpoint protection and external data back-ups. Many times, when you are hit with ransomware, it is impossible to get your files back because the payment processing may fail or the encryption keys may not work. The ransomware trend will only continue if those infected continue to pay the ransom. We cannot encourage this behaviour, so we suggest these ransoms are not paid.
Ransomware will continue to cause significant problems for many organisations, simply because their IT security mechanisms fail to protect them. Modern threats need modern and innovative solutions. It’s not enough to go through a continual ‘pay-up or wipe’ loop as these attacks become ever more popular. We also need to ask ourselves this question: “If we have ransomware that is TELLING us we’ve been hit because it wants our money, what does that reveal about our vulnerability to more convert attacks too?”








