A Kaspersky Lab security expert has uncovered a malware attack that tricked approximately 10,000 Facebook users around the world into infecting their devices after receiving a message from a friend claiming to have mentioned them on Facebook. Compromised devices were used to hijack Facebook accounts in order to spread the infection through the victim’s own Facebook friends and to enable other malicious activity. Countries in South America and Europe were hardest hit.
Between 24th and 27th June, thousands of unsuspecting consumers received a message from a Facebook friend saying that they’d mentioned them in a comment. The message had in fact been initiated by attackers and proceeded to unleash a two-stage attack when activated. The first stage downloaded a Trojan onto the user’s computer that installed, among other things, a malicious Chrome browser extension. This, in turn, enabled the second phase of the attack which was the takeover of the victim’s Facebook account when they logged back into Facebook through the compromised browser. A successful attack gave the threat actor the ability to change privacy settings, extract data and more, allowing it to spread the infection through the victim’s Facebook friends or undertake other malicious activity, such as spam, identity theft and generating fraudulent ‘likes’ and ‘shares’. The malware tried to protect itself by black-listing access to certain websites, such as those belonging to security software vendors.
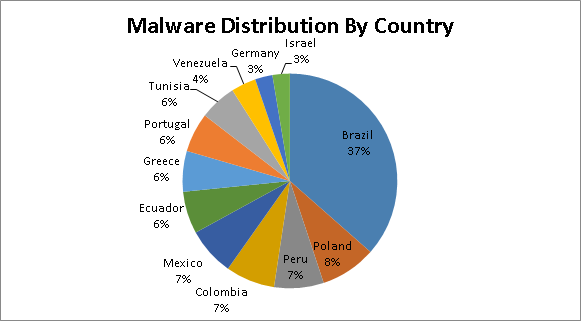
The Kaspersky Security Network registered just under 10,000 infection attempts worldwide. The countries most affected were Brazil, Poland, Peru, Colombia, Mexico, Ecuador, Greece, Portugal, Tunisia, Venezuela, Germany and Israel.
People using Windows-based computers to access Facebook were at the greatest risk, while those using Windows OS phones were also potentially at risk. Users of Android and iOS mobile devices were immune, since the malware used libraries which are not compatible with these mobile operating systems.
The Trojan downloader used by the attackers is not new. It was reported on about a year ago, making use of a similar infection process. In both the cases, language signs in the malware appear to point to Turkish-speaking threat actors.
Facebook has now mitigated this threat and is blocking techniques used to spread malware from infected computers. It says that it has not observed any further infection attempts. Additionally, Google has removed at least one of the culprit extensions from the Chrome Web Store.
“Two aspects of this attack stand out. Firstly, the delivery of the malware was extremely efficient, reaching thousands of users in only 48 hours. Secondly, the response from consumers and the media was almost as fast. Their reaction raised awareness of the campaign and drove prompt action and investigation by the providers concerned”, said Ido Naor, Senior Security Researcher, Global Research and Analysis Team, Kaspersky Lab.
Consumers who think that they may have been infected should run a malware scan on their computer or open their Chrome browser and look for unexpected extensions. If anything suspicious is present, they should log out of their Facebook account, close the browser and disconnect the network cable from their computer. Following this, they should seek a professional to check for and clean away the malware.
In addition, Kaspersky Lab advises all consumers to follow some basic cyber-safety practices:
Read more about the attack process and how to find out whether you’ve been infected and what to do if you have in Facebook Malware: Tag Me if You Can at Securelist.com.








