DDoS Attacks show no sign of slowing down
Attack Activity Increases 111 Percent Year-Over-Year
Despite increased security protections, there is a rise in the number, frequency and complexity of distributed denial of service (DDoS) attacks. In fact, no industry has been spared, and as these attacks become more sophisticated, we have seen an increasing number of organisations struggling to cope with the aftermath and negative impact these attacks can have to their revenue and corporate reputation.
The numbers don’t lie. In the first quarter of 2016 alone, Verisign observed an 111 percent year-over-year increase in DDoS attacks, with a peak attack volume of 274 gigabits per second. Attackers were highly persistent, hitting targets with sustained attacks lasting from a few hours even to a few days, while a few customers experienced repeated attacks throughout the quarter.
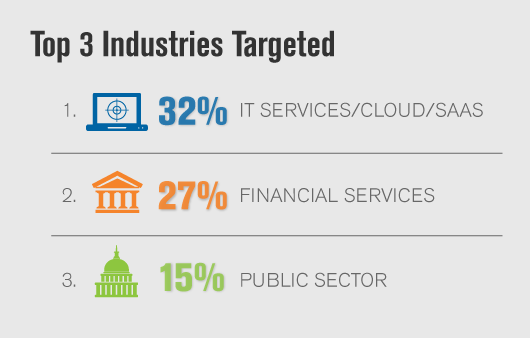
In particular, government entities across the globe, at both regional and national levels, have been frequent victims, with 15 percent of all attacks in the last quarter targeting government organisations. Public Sector organisations often find themselves a prime target for hacktivist DDoS attacks, and this is due to the fact that they are large, recognizable targets representing policies and ideologies which can draw hacktivists to rally against.
Although DDoS attacks are not a new threat to public sector organizations, the recent growth in availability and affordability in DDoS-for-hire services has made attacks on high-profile targets much easier to execute with minimal effort. Actors have flooded the networks of national government departments, academic institutions and local law enforcement websites with DDoS attacks with the intent of rendering them inaccessible.
European governments in particular have seen a recent rise in DDoS attack activity. The last quarter has seen hacktivism range from state-supported Swedish media, the Finnish Parliament and its Ministry of Defence, to the Irish government. The non-discriminatory attacks on government agencies illustrate that no organization, public or private, is immune. No matter how prepared an organization thinks it may be, DDoS attacks continue to take them by surprise, rendering services inaccessible for hours or sometimes days.
To mitigate the risk of attack, governments and businesses, both large and small, should continuously ensure they have a DDoS protection plan in place. One of the most used approaches to protect against attacks is utilising a cloud-based service, as it offers scalability, cost-effectiveness and increased security. Cloud-based managed DNS services can effectively mitigate such risk, as they provide organisations with access to dedicated experts with globally distributed networks to help ensure your company’s web presence and critical web services are always available.
The threat landscape has rapidly expanded over the past few years and shows no signs of slowing down. As the behaviour, patterns and intensity of attacks continues to shift, organisations today are finding themselves constantly having to evolve to stay secure. With major establishments in both the public and private sectors falling victim to cyber-attacks, it is critical for organisations to identify the motivations, modus operandi (MO) and objectives of adversaries in order to adequately and effectively defend their networks.