Over 40 years ago, my father broke the lock on the front door of our house. He never fixed or replaced it, so the front door was never locked – even if we all left on a week-long trip. At the same time, he religiously locked the backdoor every night. His theory was, I believe, that the back door could only be seen from one window of one neighboring house while the front door was overlooked by a half-dozen or more other homes. Long before “neighborhood watch” or “see something, say something” my dad could be sure that any anomalous behavior seen by our neighbors would be investigated and reported, if something didn’t “seem right”. That, in essence, is what Real-Time Security Intelligence (RTSI) does.
Some time ago, the concept of Security information and event management (SIEM) caught on it the IT security community. The concept was to create a central place where
All the relevant data about an enterprise’s security can be gathered from multiple locations to a central point, seen from a single point of view, making it easier to spot trends and see patterns that are questionable. There’s a huge amount of data generated by many, if not most, systems on the network. SIEM thus becomes a great forensic tool for discovering where bad things may have happened. Unfortunately, these “bad things” are rarely discovered in time to stop them from happening. SIEM remains a great forensic tool, but more is needed if we want to stop bad things from happening.
Finding bad stuff by using SIEM to sift through all of the logged entries has been characterized as finding a needle in a haystack. RTSI, on the other hand, is about seeing someone drop the needle and reporting it – and even retrieving the needle before someone accidently stabs themselves.
Real Time Security Intelligence is intended to detect threats in real time, or near real time, to enable action to be taken before damage is done. It uses techniques taken from big data and business intelligence to reduce that massive volume of security event data collected by SIEM to a small number of actionable alarms where there is a high confidence that there is a real threat.
An RTSI system is also dynamic (as opposed to a static SIEM system), constantly learning what is acceptable behavior and what is anomalous. It’s also constantly acquiring new intelligence from its vendor and other sources to keep threat profiles up to date.
A Real Time Security Intelligence system monitors users for behavior (access times, locations, data retrieved, data actions, etc.) which is different from “normal” as determined by a baseline which the RTSI system constructs and modifies over time. It also monitors data contextually, again to determine if actions are “normal” or anomalous. Additionally, the system will monitor the usual perimeter security devices, using the most up-to-date threat signatures to discover and mitigate attacks originating outside the enterprise.
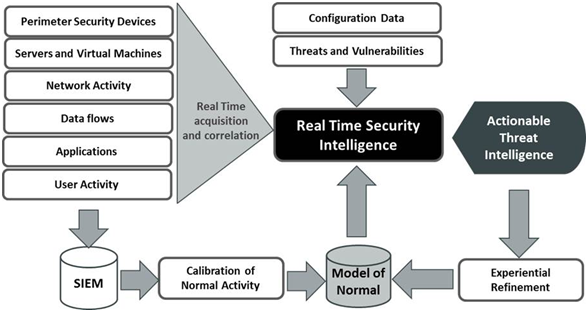
Like the neighbors my father relied on, the RTSI system is always on watch for non-trivial abnormal behavior which can be questioned, reported and stopped before anything bad can occur. Considering the cost of a breach which releases corporate proprietary information or personal data which can lead to identity fraud, or even out and out theft of money and property, the cost of an integrated RTSI system is a small price to pay, and the benefits are great.
Dave Kearns is Senior Analyst at KuppingerCole and focuses especially on the future trends around authentication and authorization and therein on risk-/context-based authentication and authorization. He attended Carnegie Institute of Technology (now Carnegie Mellon University), leaving to help found the first on-line banking system in the US, with Pittsburgh‘s Dollar Savings Bank. He spent 10 years as a network manager, ending up as Information Services Manager for the former Thomas-Conrad Corporation (now part of Compaq). In 1987, he was a founding SysOp of Novell‘s Novell Support Connection service on Compuserve and served as the first president of the Association of NetWire SysOps. Dave Kearns was formerly Technical Editor of Networking Solutions magazine. He has written, edited and contributed to a number of books on networking and is a frequent speaker before both trade and business groups.








