It’s a nightmare scenario for any IT manager, receiving a phone call to hear that hundreds of computers have been infected with ransomware, knocking critical systems offline and putting their organisation’s entire operations at risk.
That’s what happened to one large organisation earlier this year, when it found itself the victim of a carefully planned and executed ransomware attack. What was uncovered from our investigation was a perfect example of an emerging form of corporate-specific attack. While most ransomware gangs have focused on widespread, indiscriminate campaigns, a number of groups have begun deliberately targeting specific organisations in a bid to completely cripple operations and extract a massive ransom.
Many of these attacks employ the same high level of expertise we see in cyberespionage attacks, using a toolbox that includes exploits of software vulnerabilities and legitimate software utilities to break into and traverse an organisation’s network.
The attackers in our example were no different, gaining a foothold on the organisation’s network by exploiting an unpatched vulnerability in one of its servers. Using a number of publicly available hacking tools, the attackers mapped out the victim’s network and infected as many computers as they could with a hitherto unknown variant of ransomware.
The outbreak caused considerable disruption for the organisation, but it could have been much worse. Fortunately critical systems were quickly back online and much of the data encrypted by the ransomware could be restored from backups.
These kinds of attacks are still relatively rare, but now that they have been proven possible, the potential opportunity to hold well financed organisations for ransom may motivate more attacks.
Worrying trends
Symantec’s latest research paper on ransomware finds that it has now grown into one of the biggest dangers facing businesses and consumers today. 2015 was a record year, with 100 new ransomware families discovered. The vast majority of new ransomware discovered is now the more dangerous form of the threat: crypto-ransomware, which is capable of locking away the victim’s files with strong encryption.
The average ransom demand has more than doubled and is now US$679, up from $294 at the end of 2015. This year has also seen a new record in terms of ransom demand, with a threat known as 7ev3n-HONE$T (Trojan.Cryptolocker.AD) requesting a ransom of 13 Bitcoins per computer ($5,083 at the time of discovery in January 2016).
Who’s most affected?
With 31 percent of global infections, the US continues to be the country most affected by ransomware. Italy, Japan, the Netherlands, Germany, UK, Canada, Belgium, India, and Australia round out the top 10.
While the majority of victims (57 percent) continue to be consumers, the long term trend indicates a slow but steady increase in ransomware attacks aimed at organisations rather than individuals.
The Services sector, with 38 percent of organisational infections, was by far the most affected business sector. Manufacturing, with 17 percent of infections, along with Finance, Insurance and Real Estate, and Public Administration (both on 10 percent) also figured highly.
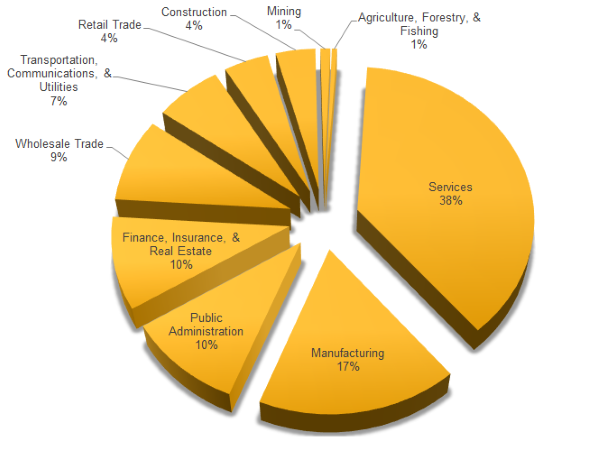
Figure. Ransomware infections by organisation sector, January 2015–April 2016
Tips for businesses and consumers
- New ransomware variants appear on a regular basis. Always keep your security software up to date to protect yourself against them.
- Keep your operating system and other software updated. Software updates will frequently include patches for newly discovered security vulnerabilities that could be exploited by ransomware attackers.
- Email is one of the main infection methods. Delete any suspicious-looking email you receive, especially if they contain links and/or attachments.
- Be extremely wary of any Microsoft Office email attachment that advises you to enable macros to view its content. Unless you are absolutely sure that this is a genuine email from a trusted source, do not enable macros and instead immediately delete the email.
- Backing up important data is the single most effective way of combating ransomware infection. Attackers have leverage over their victims by encrypting valuable files and leaving them inaccessible. If the victim has backup copies, they can restore their files once the infection has been cleaned up.
Protection
Adopting a multi-layered approach to security minimises the chance of infection. Symantec has a comprehensive strategy that protects against ransomware in three stages.
- Prevent: Email security, Intrusion Prevention, Download Insight, Browser Protection, Proactive Exploit Protection (PEP).
- Contain: Advanced signature-based antivirus engine with machine learning heuristic technologies, including SONAR and Sapient.
- Respond: Dedicated Incident Response team to help organisations respond and recover from a ransomware attack.








