Kasper Lindgaard, Director of Research and Security, Secunia Research at Flexera Software
Ah, the Internet of Things… IoT brings with it endless opportunities – and, quite a few security challenges. There is one overriding message for vendors and consumers alike – no Internet-connected device is likely to be 100 percent secure. If your device is connected to the Internet, it can likely be hacked. The problem created by vulnerabilities is more broad-based than most people – and companies – realise.
According to PwC, the average financial loss attributed to security incidents was $2.5 million in 2015, and the reputational damage and loss of trust that results from these break-ins can cut far deeper than the cost of repairing the damage. An organisation’s first line of defense to minimise criminal threats should be to diminish the attack surface, or decrease the number of vulnerabilities residing within an organisation’s environment. Taking this preventative measure will considerably lower the likelihood that a hacker can do any real harm.
Vulnerabilities are errors in software that can be exploited with a security impact and gain – and according to Flexera Software’s 2016 Vulnerability Review – they are a major concern. In 2015, a total of 16,081 vulnerabilities were recorded in 2,484 products from 263 vendors. These findings exemplify the challenge faced by all security and IT operations teams who are trying to protect their environment against security breaches every day.
However, there are clues in the data that provide insights into how to handle vulnerabilities. Of those 16,081 vulnerabilities discovered, 13.3 percent were rated as ‘Highly Critical’[1], and 0.5 percent as ‘Extremely Critical. Moreover, 84 percent of vulnerabilities in all products had patches available on the day of disclosure. This means that by implementing a proper Software Vulnerability Management strategy, organisations can significantly reduce their attack surface, and the likelihood of a successful breach.
Software Vulnerabilities
Most successful attacks use known software vulnerabilities to gain access, or escalate privileges inside corporate IT infrastructures. Once hackers have successfully exploited a vulnerability, they have a base to roll out their attack, moving around systems, collecting information and deploying malware – hostile or intrusive software, including computer viruses, worms, Trojan horses, ransomware, spyware, adware, scareware and other malicious programs – to steal or destroy business-critical information or cause disruption.
It is absolutely critical for IoT product manufacturers to have a clear Software Vulnerability Management strategy in place to greatly reduce their attack surface, and the likelihood of a successful breach. If hackers successfully launch an attack against an Internet-connected product, it can cause enormous damage to the manufacturer and its customers – either because the product is taken over, or because user data is extracted and abused by the hackers.
Consequently, IoT manufacturers need to increase their focus on security when they develop products. This includes careful code testing, continuous maintenance, careful mapping of bundled software and verified intelligence about software vulnerabilities in that software – as well as ample resources to react promptly and effectively once a vulnerability is reported.
Vulnerability Intelligence: Three Critical Stages
Vulnerability Intelligence refers to all research data on vulnerabilities – including historical data, attack vector, impact, criticality ratings and fixes. Vulnerability Intelligence can be integrated with an organisation’s security strategy to support risk assessment. And it can be used by Software Vulnerability Management to feed and enhance tools.
How is Vulnerability Intelligence derived? It starts with investigation to determine whether the numerous vulnerabilities identified globally from countless sources, actually exist. Once a vulnerability’s existence is substantiated, evaluation of its criticality is essential so that an enterprise can determine which ones pose the greater risk and require more immediate attention.
Vulnerability Intelligence feeds into the three critical stages of the Software Vulnerability Management Lifecycle.
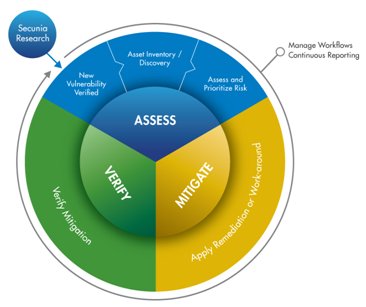
The lifecycle begins with the “Assess” stage in which the existence of the vulnerability is researched and verified. Then the organisation needs to filter out the known vulnerabilities and concentrate only on those impacting the organization. That entails comprehensive asset discovery and inventory to determine which systems are potentially threatened by the verified vulnerabilities. Once the universe of known vulnerabilities is winnowed down to only the subset impacting the enterprise, then Vulnerability Intelligence can be applied to determine which vulnerabilities are most critical, and therefore require prioritised attention.
The second stage of the Software Vulnerability Management lifecycle involves mitigation. This is often where a handoff occurs between the corporate security team and the IT Operations team (though I do not recommend a siloed approach between security and IT Operations).
The IT Operations team ordinarily handles patch management, and will use their Application Readiness processes to identify and download the applicable patches (remember that 84 percent of vulnerabilities have patches available on the day of disclosure). The patches then need to be tested (i.e. for dependencies), packaged up and distributed to the correct machines. This mitigation process must be well managed and automated to avoid system overloads and failures.
The last step of the Software Vulnerability Management lifecycle is verification, whereby the application of the patch or other mitigation technique is verified. Once mitigation is complete, the attack vector for that vulnerability has been eliminated.
Fighting Crime Proactively and Reactively
Organisations must use proactive and reactive techniques to fight crime. They must be proactive to make sure it is as difficult as possible for a hacker to break into systems. They must also be reactive, prepared to detect and respond to incidents when they happen.
Many organisations focus on reactive approaches, only dealing with the attack once it has occurred. The challenge with this approach is that it is exponentially more problematic to identify and respond to breaches when there are too many holes and cracks for hackers to exploit. And the consequences of this limited approach are reported out daily in the news headlines, especially with IoT being such a hot topic. A proactive approach via Software Vulnerability Management means investment in the people, processes and technology to successfully reduce the attack surface and decrease the likelihood that a software vulnerability can be exploited by hackers.
Organisations need to understand what IT assets exist within their environments that could be the target of attack. They need to have a complete picture of the vulnerability landscape – and more importantly, a picture of which vulnerabilities apply to them. Then finally, organisations need an accurate and reliable assessment of the criticality of those vulnerabilities, so they can prioritise remediation. A thorough program founded upon Vulnerability Intelligence will help minimise the attack surface, reducing the risk that a successful exploit can occur – and only keeping IoT in the headlines, not how thousands of your devices that access it have been malevolently hacked.
[1] Secunia Research at Flexera Software gives vulnerabilities a criticality rating based on the analysis of different aspects of the vulnerability. A description of criteria for ratings is available on page 27 of the Vulnerability Review 2016.








