Corporate security teams face numerous challenges. They need to adapt to an increasing number of sophisticated attacks and at the same time, abide by strict business processes and controls. This can impede rapid adoption of new security solutions or changes to existing ones, with organisations cautious of updating these systems in order to minimise risk of blocking business applications or communications. As a result, existing security solutions are often not leveraged as they could be.
False Negatives, an alert that should have happened but didn’t, can occur from time to time and occasionally be the precursor to a malicious intrusion or widespread infection. Companies that rely on signature based security solutions should consider the risk they may be subjected to. In situations where new threats (or yet to be discovered ones) are active in the wild without detection, any solution that rely mostly or solely on signatures may be exacerbating lack of detection.
When a new threat in the wild is discovered, security companies will protect their customers first, before publicly sharing analysis (usually via a blog post). This is especially the case with high profile Zero Days, malware campaigns and web site compromises.
Once the information is made public, security vendors that have not yet discovered the threat or lack detection capabilities will then typically respond by scrambling to update their own detection. Unfortunately this can take anywhere from hours to days, sometimes longer. This is one example of a temporary detection gap, which leaves companies exposed to threats. The duration of this gap can vary from one threat to another.
Through the use of encrypted delivery techniques and underground crypting services, malware payloads can initially not be detected. Companies might still have the ability to detect some of this obfuscated malware but often don’t due to disabling advanced features like heuristic, behavioural and cloud analysis.
The next line of defence might be network based detection if the malware is beaconing out to command and control infrastructure, but these can also be missed. If this happens, the malware can embed itself and not cause any security alerts for a sustained period.
This has been the case with many of the Point of Sale (POS) intrusions over the last few years, which have been caused by both out of date security infrastructure and false negative situations. The impact on business can be devastating. Although POS malware is typically not as widespread as commodity malware. These are designed for specific environments and can often hide in plain sight. As a result they often need to be sought out manually, as opposed to waiting for alerts.
Figure 1 – Some recent POS intrusions
Commodity malware (also referred to as Crimeware) is the most common type of malware and includes threats like ransomware, banking trojans, downloaders and AdFraud bots. Typical delivery channels for these infections are phishing emails, malvertising campaigns and compromised websites. All of which are subject to false negative scenarios where detection is not available until it’s too late.
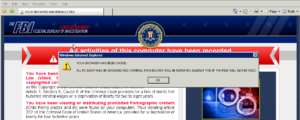
Figure 2 – Ransomware infection after being exploited by a Exploit Kit.
Unfortunately these detection gaps are set to continue unless organisations adopt an automated and integrated approach to threat intelligence. Professional cybercriminals’ ability to adapt to modern detection technologies and evade them is constantly evolving. They are continually changing hosting infrastructure, URL patterns, exploitation techniques and payloads at a high frequency, all in an effort to stay one step ahead of detections. Organisations need to be staying abreast of threat indicators by monitoring the patterns, domains and delivery channels of bad actors, in order to avoid them and reduce the impact of detection gaps. Luckily, this is possible.
Diminishing Detection Gaps with Threat Intelligence
Armed with threat intelligence, security teams can pro-actively investigate and hunt for evidence of suspicious or malicious activity associated with the threats mentioned above and more, which current security solutions may be blind to.
Some examples of leveraging threat intelligence to mitigate the impact of detection gaps when they arise can include but are not limited to:
- Tracing web based malware infections back to the source network or website
- Generating custom intrusion detection signatures
- Checking for evidence of TTPs within your environment
- Looking for Lateral Movement activity
- Checking for compromised email accounts belonging to your org or business partners
- Blocking web and email access for phishing and typo-squat domains
- Searching logs for malicious domains or URLs that are not being blocked
- Consuming feeds for compromised websites and blocking or limiting access
- Monitoring suspicious domain registrations and pre-emptively blocking
By utilising all the tools in a well-stocked arsenal, IT security teams will be in the best position to proactively detect and defend against malicious attacks, thus minimising the negative effects of a cyber breach.
Josh Gomez, Senior Security Researcher at Anomali








