Sonatype, the leader in software supply chain automation, has announced the results of its 2017 DevSecOps Community Survey which was conducted in February. There were 2,292 IT professionals that participated in the online survey which revealed that mature development organisations ensure automated security is woven into their DevOps practice, early, everywhere, and at scale. Analysis of responses also found that IT organisations continue to struggle with breaches as nearly a 50% increase was recorded between Sonatype’s 2014 and 2017 survey.
The adoption of DevOps around the world is evidenced by 67% of survey respondents describing their practices as very mature or of improving maturity. Where traditional development and operations teams see security teams and policies slowing them down (47%), DevOps teams have discovered new ways to integrate security at the speed of development. Only 28% of mature DevOps teams believe they are being slowed by security requirements.
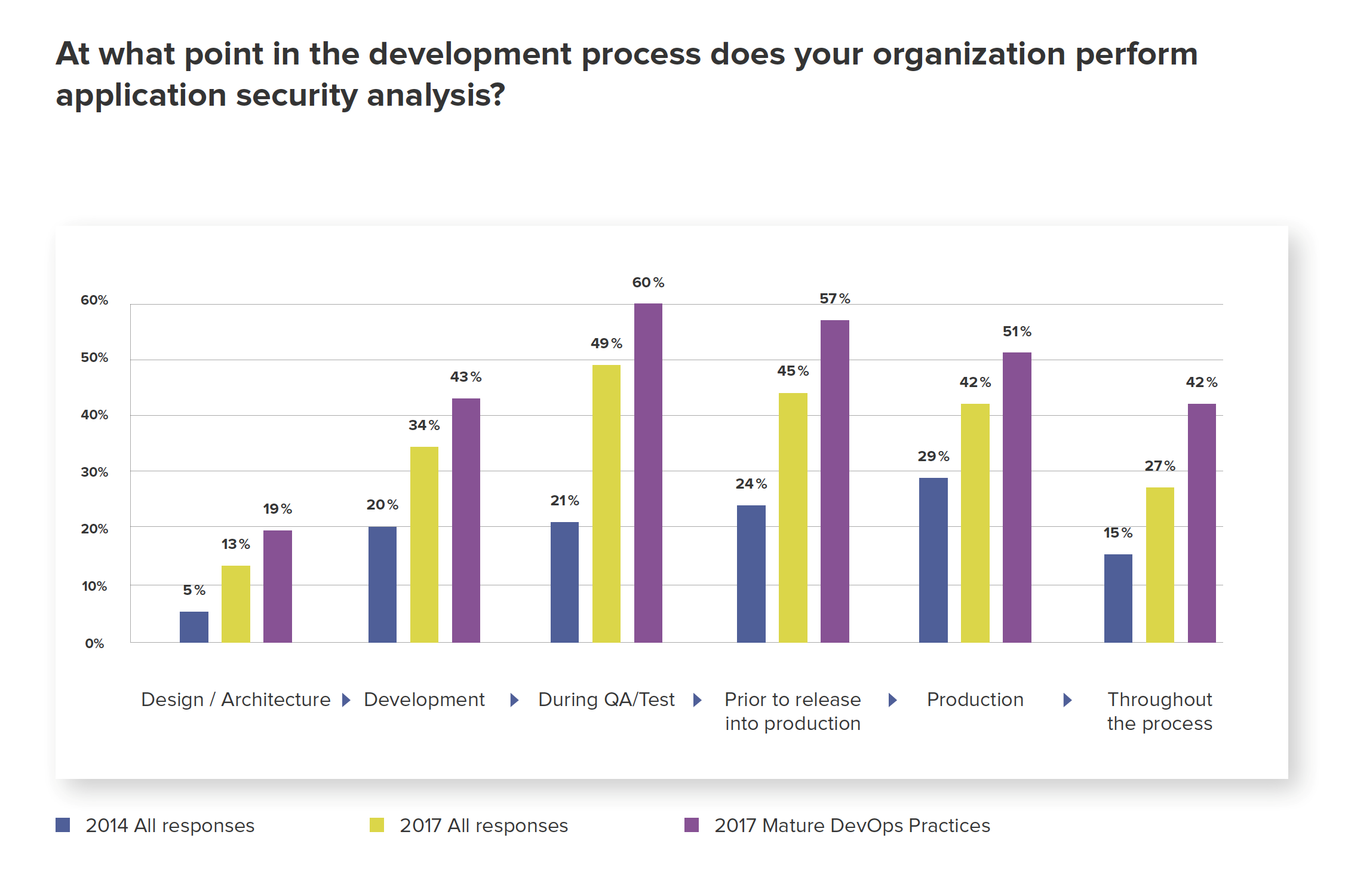
Other key findings from the survey include:
Development plays an active, early role in application security
- Developers are taking more responsibility for security with 24% of all respondents saying it’s a top concern while in mature DevOps organisations that number rises to 38%.
- 58% of mature DevOps teams have automated security as part of Continuous Integration (CI) practices compared to 39% of all survey participants.
For DevOps teams, security controls are increasingly automated throughout the development lifecycle
- 42% of mature DevOps organisations perform application security analysis at every stage of the software delivery life cycle (SDLC). This number shrinks to just 27% when all survey respondents are counted.
Automated security practices allow developers to keep pace with the speed and scale of innovation
- 88% of survey respondents indicated that security was a top concern when deploying containers, yet only 53% leverage security solutions to address this problem.
- 35% of organisations keep a complete software bill of materials to help them track down new open source vulnerabilities faster (e.g., Commons-Collection, Struts2).
- 85% of those surveyed from highly mature DevOps practices received some form of application security training, ensuring awareness of secure coding practices. In immature DevOps practices, 30% received no training.
“As evidenced by this year’s survey results, organisations everywhere are now transforming their development from waterfall-native to DevOps-native tools and processes,” said Wayne Jackson, CEO, Sonatype. “Along the way, they are coming to grips with one simple fact: DevOps is not an excuse to do application security poorly; rather it is an opportunity to do application security better than ever.”
View the full survey








