Centrify, a leading provider of cloud-ready Zero Trust Privilege to secure modern enterprises, today announced results of a new survey revealing that most IT decision makers are not prioritising Privileged Access Management (PAM) practices and solutions, despite knowing privileged credential abuse is involved in almost three out of every four breaches.
The survey of 1,000 IT decision makers, 500 from the U.K. and 500 from the U.S. found that, of those whose organisations have experienced a breach, 74 percent acknowledged it involved access to a privileged account. This number aligns with Forrester’s estimate that 80 percent of security breaches involve compromised privileged credentials[1].
However, despite being aware that they’ve been breached, the survey results show that most companies are still extremely immature in their PAM journey:
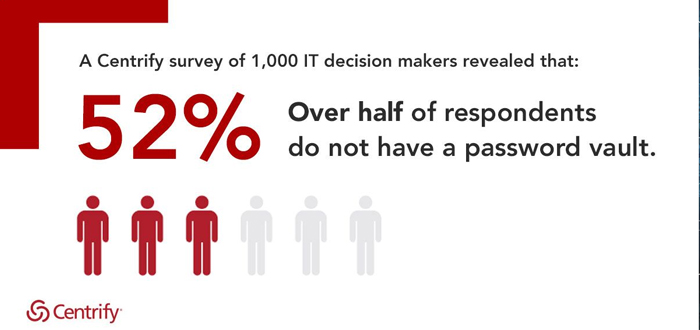
52 percent of respondents do not have a password vault (60 percent of U.K. respondents)
65 percent are still sharing root or privileged access to systems and data at least somewhat often (58 percent of U.K. respondents)
63 percent indicate their companies usually take more than one day to shut off privileged access for employees who leave the company (70 percent of U.K. respondents)
21 percent still have not implemented Multi-Factor Authentication (MFA) for privileged administrative access (27 percent of U.K. respondents)
Tim Steinkopf, CEO of Centrify comments: “Forrester had already estimated that privileged credential abuse was the leading attack vector, but now we have the empirical research to back it up. What’s alarming is that most organisations aren’t taking the most basic steps to reduce their risk of being breached.
“It’s not surprising that Forrester has found 66 percent of companies have been breached five or more times[2]. It’s well past time to secure privileged access with a Zero Trust approach, and many organisations can significantly harden their security posture with low-hanging fruit like a password vault and MFA.”
The survey also revealed that, generally, respondents in the U.K. are behind their U.S. counterparts when it comes to securely managing privileged access. Forty-four percent of U.K. IT decision makers surveyed were not positive what Privileged Access Management is, and 60 percent do not have a password vault. This also affects their confidence in the ability to secure their organisations, as only 36 percent of U.K. respondents are “very confident” in their company’s current IT security software compared to 65 percent of U.S. respondents.
“Centrify believes that reason for this increased prioritisation and spending on PAM is the increasingly-modern threatscape that security professionals are facing,” Steinkopf continued. “Today’s environment is much different than when all privileged access was constrained to systems and resources inside the network. Privileged access now not only covers infrastructure, databases and network devices, but is extended to cloud environments, Big Data, DevOps, containers and more.”
Indeed, the survey found that respondents are not controlling privileged access to these modern use cases, including:
45 percent are not securing public and private cloud workloads with privileged access controls (53 percent of U.K. respondents)
58 percent are not securing Big Data projects with privileged access controls (63 percent of U.K. respondents)
68 percent are not securing network devices like hubs, switches and routers with privileged access controls (72 percent of U.K. respondents)
72 percent are not securing containers with privileged access controls (73 percent of U.K. respondents)
Centrify is redefining legacy approaches to PAM with cloud-ready Zero Trust Privilege. To download a complimentary copy of the survey results, please visit https://www.centrify.com/resources/centrify-privileged-access-management-in-the-modern-threatscape-2019/
For more information about Centrify Zero Trust Privilege, visit https://www.centrify.com/education/what-is-zero-trust-privilege/