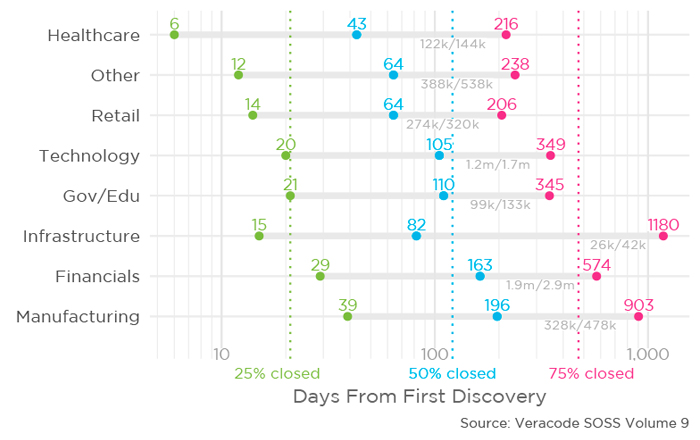
Veracode’s State of Software Security report (SoSS) revealed the healthcare sector is the fastest industry when it comes to addressing common vulnerabilities found in software. The global report found healthcare organisations took only six days to address a quarter of their vulnerabilities in code and just seven months (216 days) to remediate the majority (75%) of vulnerabilities. That’s almost eight months faster than the average organisation who is taking 15 months (472 days) to fix 75% of its vulnerabilities.
The sensitive data held by healthcare organizations are a significant target for evolving threats. A focus on code quality can help healthcare organizations shift from a reactive security stance to a proactive one. A significant 64% of current applications used by healthcare organisations are at risk of information leakage attacks, wherein an application reveals sensitive data that can be used by an attacker to exploit a web application or its users. Cryptographic issues (62%) and code quality (60%) round out the top three vulnerabilities facing healthcare organisations and provide areas of focus for improvement within the NHS and other health service agencies.
Healthcare organisations are perceived to be behind the times with technology and have larger installations of legacy software, however, Veracode’s analysis shows healthcare companies are not hindered in staying on top of application security. The sector ranks first for the latest scan OWASP pass rate, and based on the flaw persistence analysis chart, the industry is statistically closing the window on application risk faster than any other sector. The State of Software Security report also studied vulnerability remediation in retail, technology, public sector, infrastructure, finance and manufacturing.
“Healthcare organisations are remediating at the most rapid rate at every interval compared to their peers. It takes just a little over seven months for healthcare organizations to reach the final quartile of open vulnerabilities, about eight months sooner than it takes the average organisation to reach the same landmark,” said Paul Farrington, EMEA Chief Technology Officer at Veracode. “It shows remarkable resilience for an industry which was heavily targeted and badly damaged during the WannaCry ransomware attack two years ago. However, millions of cyber-attacks are aimed at the healthcare sector each day, seeking any weak spot. Using code that is secure from the start can help healthcare reduce security risk further.”
The NHS recently announced that it is undertaking an IT overhaul to use cloud-based, modern systems and improve security. With this in mind, developers and security professionals in healthcare need to focus on building on this “first place for fixes” position and pursue DevSecOps models of frequent, incremental software scanning. This will ensure they are able to remediate application flaws even more quickly and efficiently.
Read the full State of Software Security volume 9 report here.
About Veracode
With its combination of automation, process, and speed, Veracode becomes a seamless part of the software lifecycle, eliminating the friction that arises when security is detached from the development and deployment process. As a result, enterprises are able to fully realize the advantages of DevOps environments while ensuring secure code is synonymous with high-quality code.
Veracode serves more than 2,000 customers worldwide across a wide range of industries. The Veracode Platform has assessed more than 10 trillion lines of code and helped companies fix more than 36 million security flaws.
Learn more at www.veracode.com, on the Veracode blog and on Twitter.