Review by: Dave Mitchell
Supplier: CyCognito
Website: www.cycognito.com
Price: Based on number of assets
Scores
Performance 5/5
Features 5/5
Value for Money 5/5
Ease of Use 5/5
Overall 5/5
Verdict: With data protection regulations getting ever stricter, failure is not an option. CyCognito is a new breed of security assessment platform that can keep you one step ahead of the hackers.
The sheer scale of high-profile data security breaches show that even now, too many businesses are still not taking this seriously. These are not trivial breaches either, as in many incidents organised gangs of criminals have been able to steal millions of records containing sensitive and personal data.
The damage done to a business’s reputation is bad enough but punitive fines can bring them to their knees. To show it means business, recent GDPR (General Data Protection Regulation) legislation has increased the maximum penalty for severe violations to up to €20m or 4% of global turnover – whichever is greater.
Clearly, businesses need to implement robust cybersecurity measures but many products are fragmented and complex to deploy, making them unappealing to stressed-out security officers. The CyCognito Platform takes a refreshingly different approach as it requires no configuration, no additional resources and virtually no information about the company being protected.
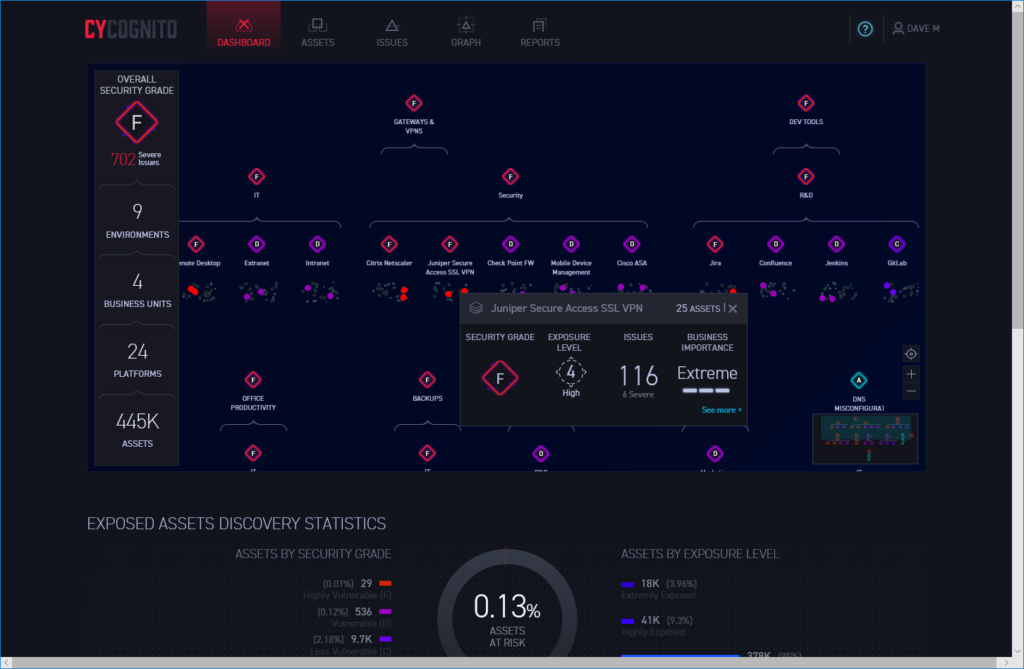
The portal’s dashboard provides an overview of all assets, their grouping and security posture
Zero installation and deployment
CyCognito takes the view that a security assessment solution should behave in the same way as a hacker. Those intent on attacking a specific organisation will look for the assets they own, which ones are exposed and what vulnerabilities can be exploited.
Some solutions require information about an organisation that a hacker may not be able to glean through conventional methods giving them a biased perspective. Others may require agents installed inside the network perimeter creating, an unrealistic monitoring environment.
All CyCognito requires from the customer is one detail about its domain or just the company name – a snippet of information a hacker can easily acquire. It doesn’t use agents and needs no further insider information such as IP addresses.
CyCognito’s cloud-based reconnaissance platform then sets about finding out everything it can about the organisation, using the same techniques as hackers. The company employs a global network of over 60,000 bots that look for information on the internet about company resources to determine its attack surface.
This requires no user intervention or configuration and is completely external to the organisation. CyCognito maps the organisation and its perimeter and starts continuous and autonomous security testing on all discovered assets.
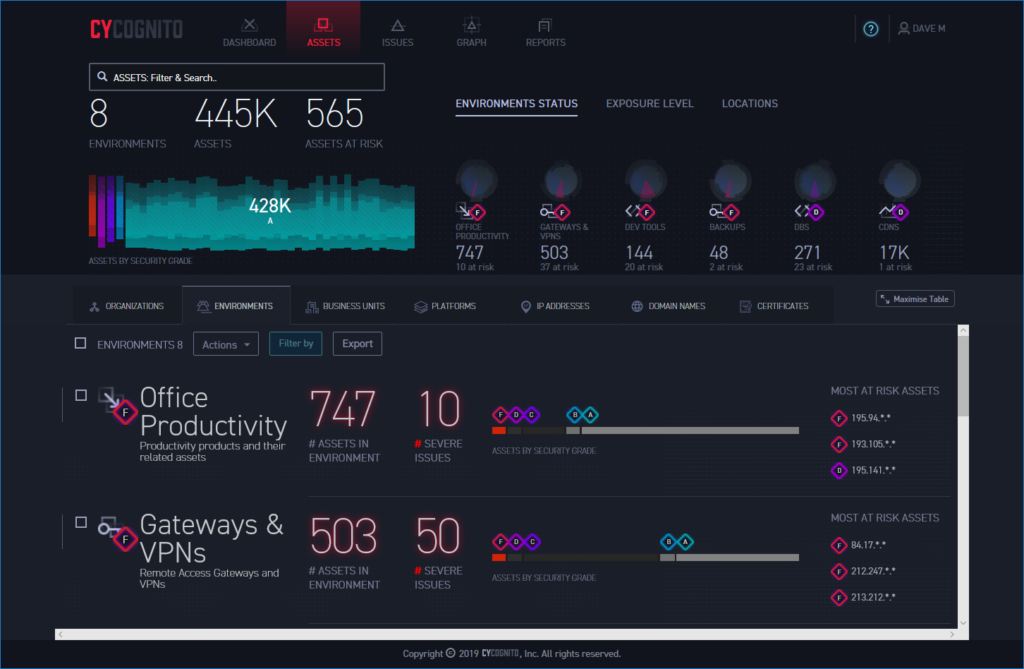
The Asset view shows all critical vulnerabilities which can have filters applied
Voyage of discovery
CyCognito’s classification engine probes exposed assets to understand what is in front of it. These can be anything from a firewall, gateway or SSL VPN appliance to a database application or web-based service.
It looks at the ease with which specific assets were discovered and how attractive their resources could be to hackers. It then conducts a deep assessment using a range of techniques to look for attack vectors including known vulnerabilities, missing patches or firmware upgrades, weak login credentials and much more.
Discovery paths are important as CyCognito builds maps showing all hops along the path to the asset. A valuable feature is its ability to discover assets that may appear not to belong to a company but are in fact, third party assets, which could easily present a back door into the company network.
This smart approach has many other benefits as all too often, breaches occur on systems or applications that an organisation wasn’t even aware it still owned. Old unpatched databases, for example, are very attractive to hackers as they can be easily exploited.
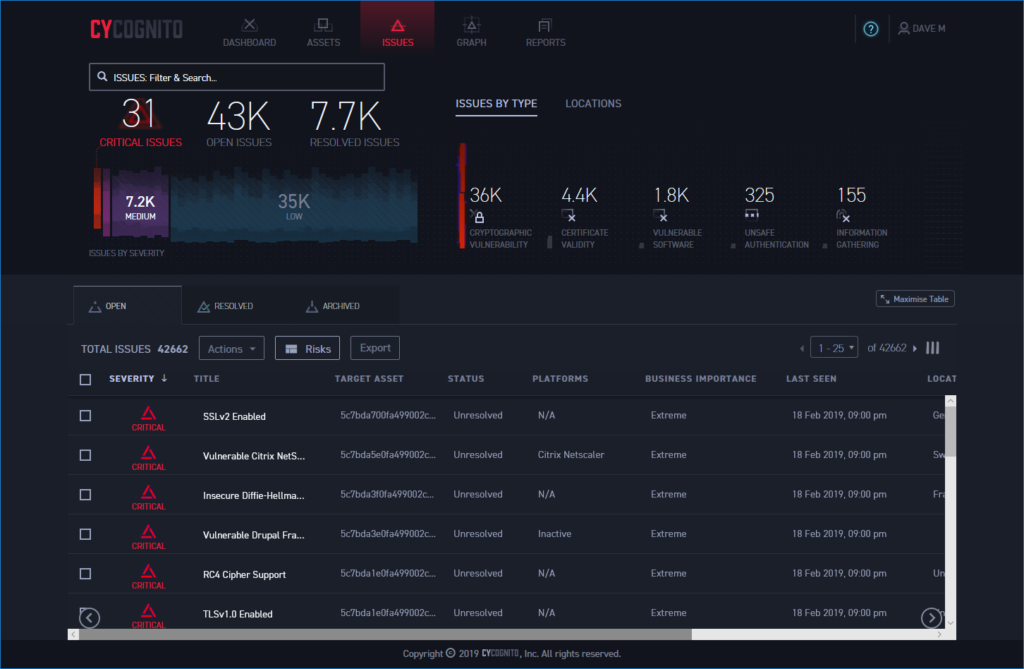
The Issues page lists all critical events first so you know what needs to be focused on
The CyCognito portal
All organisational information is presented in a slick web portal that opens with a dashboard view showing real-time data, discovered assets, exposure levels and issues graded by severity. We found it remarkably informative as its hierarchical map view shows all assets that share the same business purpose automatically grouped into different environments.
One minor criticism is the portal’s ‘dark mode’ colour scheme can make it difficult to see some information. However, CyCognito advised us that an option to swap to a white background is on the product roadmap.
Along with environments, assets are grouped into business units to show which departments in the organisation are using them. You can see at a glance where vulnerabilities exist as assets, environments and business units are all assigned one of five security grades where ‘A’ is very strong and ‘F’ is highly vulnerable (there isn’t an ‘E’ grade).
CyCognito uses colour-coded icons for each grade so you can see which issues need to be prioritised. You can drill down deeper for more information as clicking on any element in the map brings up a window with more details about the exposure level, affected assets and a business importance grading.
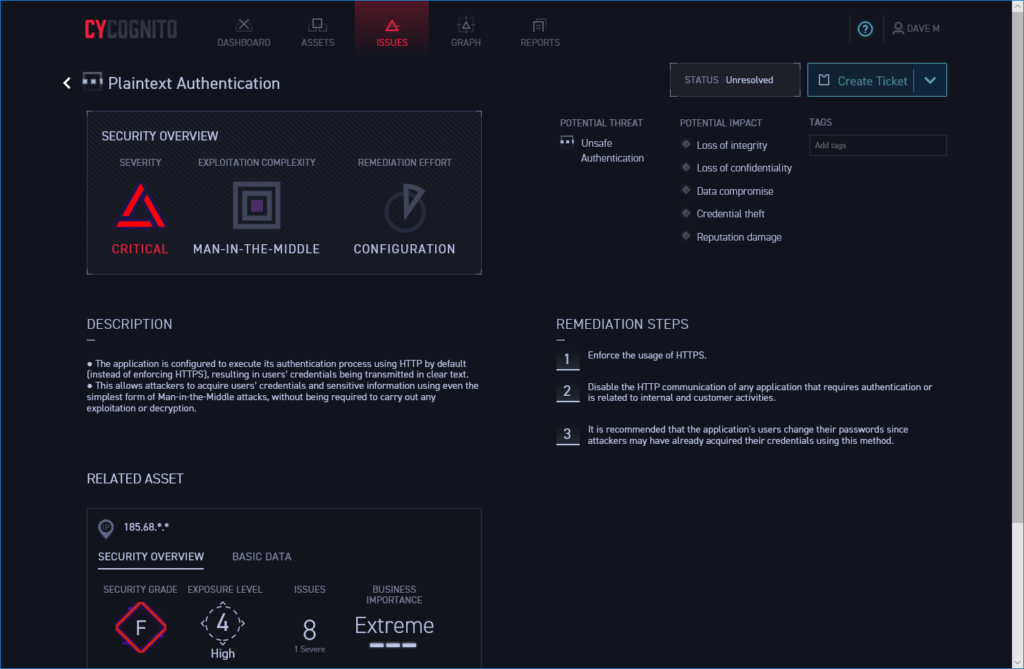
CyCognito provides plenty of valuable advice on remedial action
Assessment and remediation
The Assets window provides even more detail about attack surfaces, security issues and risks. Clicking on any element in the main page or on the active graph creates a filter to fine-tune the information being presented and you can easily see which organisation, environment, business unit and platform are affected.
Filters can be customised from the drop-down menu so views of assets that have the same, or similar, security issues or the same exploit complexity can be quickly produced. If you want to see all those classified as having vulnerable software or are prone to a man-in-the middle exploit, the list is only one click away.
CyCognito doesn’t just deliver pinpoint accuracy on where your vulnerabilities are, it also provides sage advice on fixing them. The Issues window lists all security risks in order of severity and selecting one presents an overview which clearly describes what the problem is, how it can be exploited and precisely what you need to do to rectify it.
Reporting is another strength as security teams can create them for specific areas of interest and export them as PDFs complete with hot links that take the reader back to web portal. CyCognito also integrates with existing workflows and works with the ServiceNow and Altassian Jira ticketing systems.
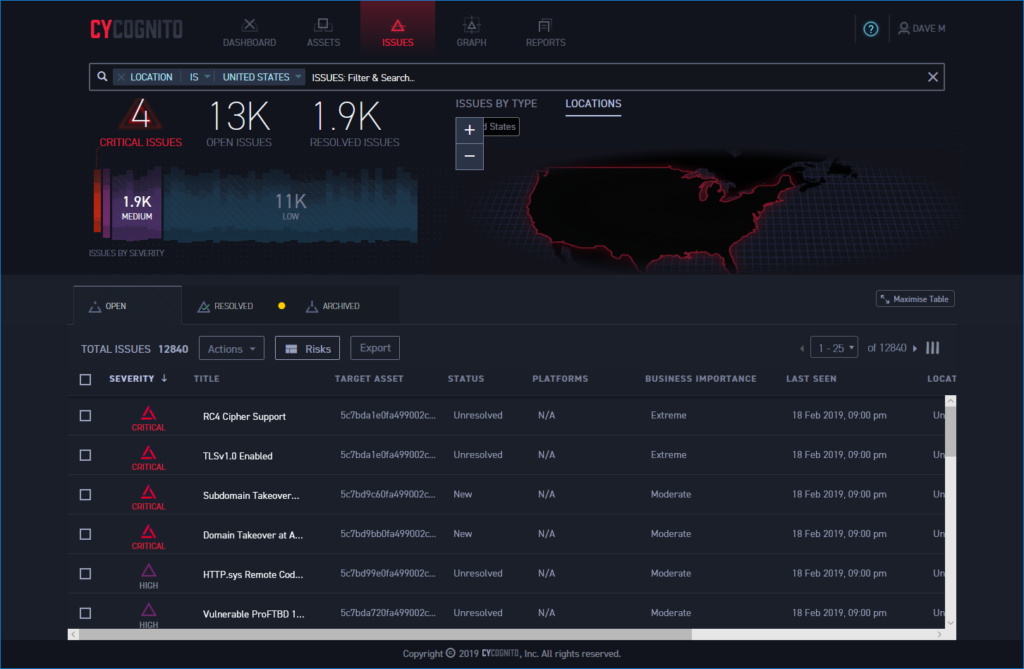
Filters for issues can be used to find the geographical location of vulnerable assets
Conclusion
The CyCognito Platform offers an innovative approach to security assessment that requires virtually no resources to use and yet is capable of presenting a vast amount of information about all exposed business assets and their security posture. By taking the hacker’s point of view, it shows businesses where their most serious vulnerabilities are, allowing them to focus their security investment where it’s needed most.








