In what now seems like a lifetime ago, in late summer 2019 Gartner first coined the phrase Secure Access Service Edge. Since then, “SASE”, as it is now more commonly referred, has generated the kind of hype the industry hasn’t witnessed since SD-WAN first emerged around 2014. The promise was simple enough: enable enterprises to realise all of the long-held (but never fully realised) benefits of moving applications and workloads to the cloud and maintaining security.
Now, seemingly every security vendor has a SASE play and marketing message to go alongside it. These messages, however, don’t always align. A wide variety of differing perspectives have emerged from vendors and the media about SASE. Some herald it as a pure replacement for SD-WAN, others say that security is the primary function, with SD-WAN features a minor value add.
This diversity of messaging and positioning can cause additional confusion for enterprises trying to wrap their heads around the SASE topic. At its most basic level, Gartner defines SASE as the combination of SD-WAN and cloud-delivered security services. SD-WAN functions as a core component of the SASE architecture, and the combination of SD-WAN and cloud-delivered security ultimately deliver on the vision for a secure access service edge.
If you want to learn more about SASE, or perhaps you’re looking to implement the framework within your own business, or out of pure interest, in this article I will share the basic principles around SASE, and offer some general, applicable tips for getting started.
The beginnings of a SASE architecture
Typically, when building a SASE architecture an enterprise might start with just one transformational project. However, by the end of the project both WAN and security architectures must be transformed. This is because traditional WAN and security architectures are ill-suited for SASE. Routers and next-gen perimeter firewalls maintain security by backhauling cloud-destined app traffic through their data centres or hub sites (Figure 1). Unfortunately, this adds latency which impairs cloud application performance.
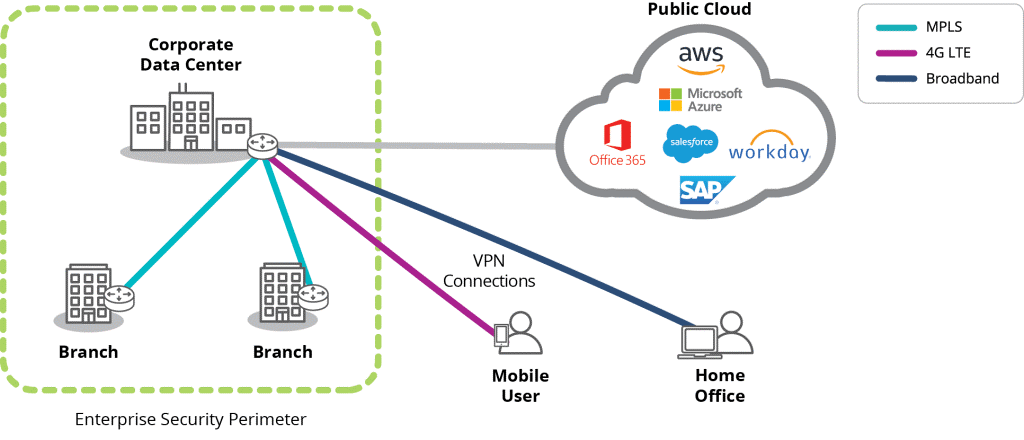
To eliminate this latency, SASE transforms both networking and security architecture, connecting branch site users directly and securely to cloud applications and services through the internet alongside cloud-delivered security services.
The Network Transformation
Looking at network architecture, the SASE model pushes for a simplified or thin WAN edge. What this entails is placing only the required network functions at the edge, and in a single unified platform which wraps up: SD-WAN, routing, stateful zone-based firewall, advanced segmentation, WAN optimisation and application visibility and control.
The Security Transformation
As applications are increasingly hosted and accessed from anywhere (a very important point within the current remote working situation), traditional perimeter-base security models are no longer effective.
In the SASE architecture, rather than hosting security services on complex to manage (and costly) next-gen firewalls within branch offices, it is far better to shift toward cloud-delivered security services. Ensuring that threat detection and mitigation capabilities are updated is far easier when these solutions are centralised within the cloud. In the same manner that SD-WAN replaces routers at branch offices, so too do cloud-delivered security services replace next-gen firewalls.
The Need for Automation
With SD-WAN and cloud-delivered security the necessary base components for SASE, any business looking to implement a secure access service edge will need to invest in SD-WAN first and foremost. SD-WAN is a healthy technology market and there are a lot of options out there. Advanced SD-WAN solutions, which are required to fully enable SASE, should rely on automated orchestration capabilities to ensure the complex infrastructure can run intelligently without too much oversight.
Automation should cover four key areas. Firstly, your SD-WAN solution should have the capability to automatically identify and classify applications on the first packet and dynamically steer them in accordance with centrally defined QoS and security policies. Secondly, it should enable the automation of the orchestration between the SD-WAN and proximity-based cloud-delivered security services from a single console.
Third is the automated reconfiguration of the primary and secondary virtual tunnels to cloud security points of presence if a newer, closer location to the branch is deployed. This helps further minimise application latency. Lastly, and most importantly, any set up should be able to automatically failover to a secondary cloud security enforcement point should the primary become unreachable, so as to maintain application availability.
Don’t put your eggs in one basket
Finally, as SASE is an ever-evolving framework, it is important that businesses avoid vendor lock-in, which provides the freedom of choice to adopt new security innovations as they emerge. Gartner itself predicts that by 2023, 20 per cent of enterprises will deploy a range of capabilities (it cites SWG, CASB, ZTNA and branch FWaaS) from a single vendor. That’s four times as many as we’re seeing today. It’s much wiser to deploy a thin WAN edge platform that incorporates deep cross-vendor integration. This ultimately provides the best of both worlds.
Contributed by Derek Granath, VP, Product and Technical Marketing, Silver Peak








