Q1/21 a symposium was hosted in the US under the title ‘Thinking Outside the SCIF’ (Sensitive Compartmented Information Facility) to put forward the case for the utilisation of OSINT (Open Source) within the US Military and Intelligence Communities.
John McLaughlin (CIA) kicked off day one by correctly pointing out that there was nothing new about open-source (OSINT), and paid tribute to how, in the conditions of the Pandemic, the utilisation of OSINT methodologies within the US Intelligence Community had effectively enabled the practicality of working out-of-office. McLaughlin went on to expand that he believes OSINT also solves the security clearance problem: “I see how long and painful the security clearance process can be” – here I can attest that as a positive factor based on my own experience. When I was undergoing the process of Enhanced Positive Vetting (EPV) to grant access to a SCIF, it took nearly seven months to complete! I see a key positive advantage to Thinking Outside the SCIF is cost saving. For example, back in the nineties my EPV cost in excess of £30,000 to carry out (and that is just for one person) – a further benefit is given the world of Compartmented Security, in the Physical sense, this approach also addresses a saving of power for the warning Red Lights alerting the presence of Uncleared Visitors in the physical locality of the SCIF (tongue in cheek comment).
This new age of the US OSINT Landscape can be seen at Fig 1 below, showing the breakdown and areas of the Electronic Theatres of Interest.
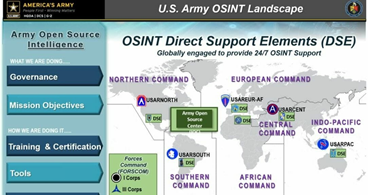
The overall OSINT Landscape at Fig 1 will be further underpinned with Project Northern Raven as another facet to leveraging inter-country collaboration. The overall aim being to improve OSINT sharing and training between partner International Nations, one of which is the UK.
Whilst this is a positive step, and a leading foot to see OSINT entering the serious conversation of Military and Homeland Security vocabulary, I am pondering as to why has it taken so long to arrive at a seemingly obvious conclusion!
Global Intelligence Gathering
For decades, the world has been defended by SIGINT (Signals Intelligence) and COMINT (Communications Intelligence) hand-in-hand with eyes-on SATCOM Intelligence (TK/Talent Keyhole) and HUMINT (Human Intelligence) to discover conditions of a potentially adversarial, dangerous nature. It is here when we add the fifth dimension in the form of OSINT, that we see the clear advantage of an extra layer of Intelligence which is derived from traversing and scraping the Internet open sources. These snippets may take the form of Data Leaks, P2P Communications, Metadata extractions, GPRS and EXIF image associated data. In isolation many of these may look meaningless, however, when aggregated they can convey a very colourful and powerful intel image to the eye of the analyst.
It may also be the case that on occasions there will be a fine balance between what is (was) an open source, which may be subjected to further analysis leading to the discovery of, what was up to that juncture a closed source – say by exploitation of the open, to discover what was closed!
Hands-On Activities
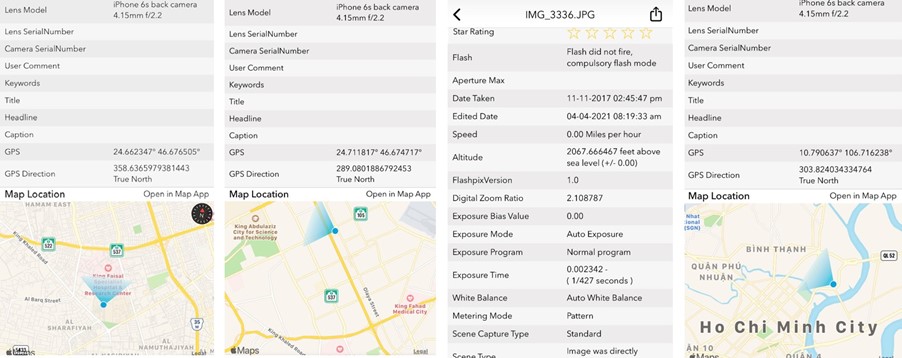
I have for many years have both practised, and taught OSINT Techniques and Methodologies to Commercial and Military clients in the UK, EU, the Saudi Arabian MOD, and the Malaysian Military Academy based in KL, to name a small selection. The advantages of OSINT are very credible, and on occasions can reflect the potential of Minority Report style predictive powers by uncovering what were unknown unknowns and morphing them into known unknowns. From that perspective it is possible to then mitigate or manage that exposure or vulnerability. It may be that you are searching to discover system weak digital point(s), or to underpin investigations seeking out paedophiles, people smugglers or other such entities. In this sphere this may achieved with zero cost, or commercials tools. For example, special browser-based applications such as Paliscope to run a mission to document the case, and cross-map the associations of EXIF data to identify locations, and say the concerned actors, at times, right to their own dirty front door – See Fig 2 showing EXIF data acquired from an iPhone.
Another powerful OSINT technology is that of Facial Recognition, which has a multitude of uses for the OSINT Operative. It can provide them with the ability to cross match, and locate images based on the facial profile, pulling from discoveries and locations at which they have been detected. This is a powerful technological medium, which has multiple uses which are only restricted by the imagination of the analyst. Interlink this with the acquired image EXIF and Metadata, and it may be (and has been) that the derived intelligence which has been acquired can be exploited to track down OCG (Organised Crime Gangs) involved in Human Trafficking, or OCG involved in the sub-world of providing Global Prostitution Services.
At Fig 3 below is a face you may recognise which has been subjected to a Facial Recognition Search.
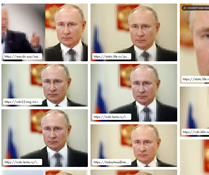
Or, for example using pimeyes to search out the sites showing images of the GRU agents who were active in Salisbury to poison Sergei and Yulia Skripal on 4 March 2018 which has discovered 786 results of related facial profiles.
OSINT is also a double edge sword and can be used for both good and evil purpose. For example, it has been a long known, yet an ignored fact, that most successful cyber hist attacks have a pre-attack OSINT run to map the digital assets, to locate any potential holes in what may be thought of as a Cuckoos Egg Style discovery mission. It may be that, again utilising specialist tools the operator may be looking for poorly deployed DNS configurations, an Open Zone Transfer opportunity, or Digital Certificate which may be used to facilitate extended access to the Corporate Crown Jewels.
On the downside of OSINT, very few Commercial Organisation have yet to appreciate just how OSINT can expose their businesses to exploitation by criminal, and say State Sponsored electronic passers-by who may view their assets as attractive. Remembering that as long ago as April 2010 a Cabinet Office, Government Security Secretariat Quarterly Threat Update notified the following:
‘Threat from electronic attack from Russian and Chinese sources was classified as SEVERE’
You have been warned!
Embracement of the GreyZone
A further concern is, from the world of Penetration Testing they need to avert their focus away from the overindulged obsession with IP and look to the associated surrounding elements which by minute implication, may be potentially waiting to be the next stepping-chip for a successful cyber-attack or compromise. In this area a significant amount of education and effort needs to be done to close this swinging stable door.
Mobility
It is of course important when handling and processing sensitive case related acquisitions and discoveries to ensure they are, as far as is practicable, compartmented from the normal day data assets (particularly important when working outside the SCIF) and protected from any potential unauthorised prying eyes. My approach in this area, and even more so when travelling outside the UK, is to store all my OSINT tools, and acquired objects on a FIPS/140-2 Encrypted Drive – this is a 2TB DiskAshur M2. See Fig 4 below which provides the additional protection of the durable physical design.

Conclusion
Overall, the initiative of Thinking Outside the SCIF is great progress, and it sees OSINT Methodologies and Technologies finally getting the public recognition that has been long-awaited for well over a decade. What we need to see now is the Corporate World to embrace these GreyZone methodologies to the secure advantage of their own systems and deployments. However, having taught these grey methodologies to Commercials and Students over the last decade, what can be one of the most challenging areas is to get the student looking at the Matrix style of flowing green bits, bytes, and objects, and translate the observed nonsensical value into meaningful intelligence – it is here where, in my opinion, the trained mind of the military world of intel can prove to be a key enabler.
Finally, in a world which has embraced the Internet, cell phones, and a life lived on-wire, there is an urgent driven need to recognise the value of what Open Source can provide as a positive step toward digital security. The key challenge is to educate to the adoption and use such technologies in a preventative guise, before they are reversed and used adversely against the business.
 Contributed by professor John Walker, Head of Consulting & Witness Expert Programmes at CIP. John is also the Editor in Chief at the International Journal of Cyber Forensics and Advanced Threat Investigations (CFATI), Visiting Professor at the School of Science and Technology NTU, and a Trainer in the Middle East delivering Certified Cyber Security, Digital Forensics – Investigations, and Cyber Intelligence specialist courses. John served in the RAF for 22 years in the roles of Policing, advancing into the world of Counter-Intelligence, working with UK Agencies such as GCHQ/CESG, and US DC based ‘specialist’ Intelligence Agencies in the areas of SIGINT, COMINT and Satellite Communications. John has held the position of system ITSO for CIA SCIF Accredited Systems. Post the RAF he held roles in IT/Cyber roles for Logica, GM, Experian, Betfair, Palace of Westminster and provided Consultancy to the Saudi Arabian MOD, and the Military Academy of Malaysia (KL) on Digital Forensics and OSINT. Currently John works in the area of specialisation in the field of Geopolitics in the Middle East.
Contributed by professor John Walker, Head of Consulting & Witness Expert Programmes at CIP. John is also the Editor in Chief at the International Journal of Cyber Forensics and Advanced Threat Investigations (CFATI), Visiting Professor at the School of Science and Technology NTU, and a Trainer in the Middle East delivering Certified Cyber Security, Digital Forensics – Investigations, and Cyber Intelligence specialist courses. John served in the RAF for 22 years in the roles of Policing, advancing into the world of Counter-Intelligence, working with UK Agencies such as GCHQ/CESG, and US DC based ‘specialist’ Intelligence Agencies in the areas of SIGINT, COMINT and Satellite Communications. John has held the position of system ITSO for CIA SCIF Accredited Systems. Post the RAF he held roles in IT/Cyber roles for Logica, GM, Experian, Betfair, Palace of Westminster and provided Consultancy to the Saudi Arabian MOD, and the Military Academy of Malaysia (KL) on Digital Forensics and OSINT. Currently John works in the area of specialisation in the field of Geopolitics in the Middle East.








