Vulnerabilities in enterprise IT are everywhere. While it’s clear that they need to be addressed, how to do so isn’t as clear.
The sheer number of vulnerable software versions in an enterprise environment can be overwhelming, making it challenging to address them. The process requires time: to identify the need for an update, to create and test a successful update package, and then to deploy that throughout the environment. As a result, it isn’t realistic to believe that an organization with thousands of applications can simply keep all of them up-to-date. Instead, security typically drives a remediation process, issuing priorities to IT operations.
A more efficient process is required to view, prioritize, and manage software vulnerabilities—and lower the security risk to the entire organization. Here are 3 steps to improve vulnerability management.
1. Understand your end-of-life and end-of-support risk.
Cybersecurity risk is present throughout the IT stack, but the risk presented by end-of-life or end-of-support (EOL/EOS) software is particularly worth monitoring and mitigating. Any software that’s reached EOL or EOS must be considered vulnerable. Why? Because it is no longer receiving the attention necessary to qualify it as otherwise.
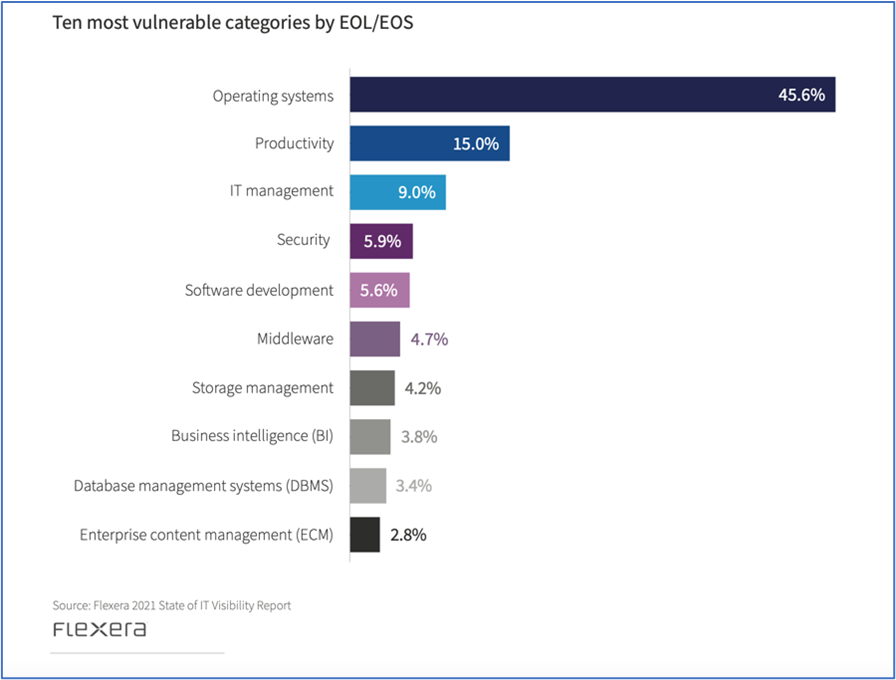
The Flexera 2021 State of IT Visibility Report found that operating systems and productivity software lead the pack in terms of EOL/EOS vulnerabilities. Across all categories, it is important to maintain detailed information about the specific versions and releases that you’re using. This can facilitate identification of areas that need attention. Monitoring EOL/EOS dates is also an important component of an overall software asset management (SAM) effort so you can stay ahead of what versions of products in your environment will reach EOL/EOS in the weeks ahead.
Collaborating across the enterprise can help strengthen your EOL/EOS strategy. Even though lifecycle management impacts the whole organization, EOL/EOS data is often siloed within an organization. Instead, sharing it—including the EOL/EOS dates—among teams (including IT management and support, procurement, and finance) can help ensure your overall security stance.
2. Streamline IT decision making.
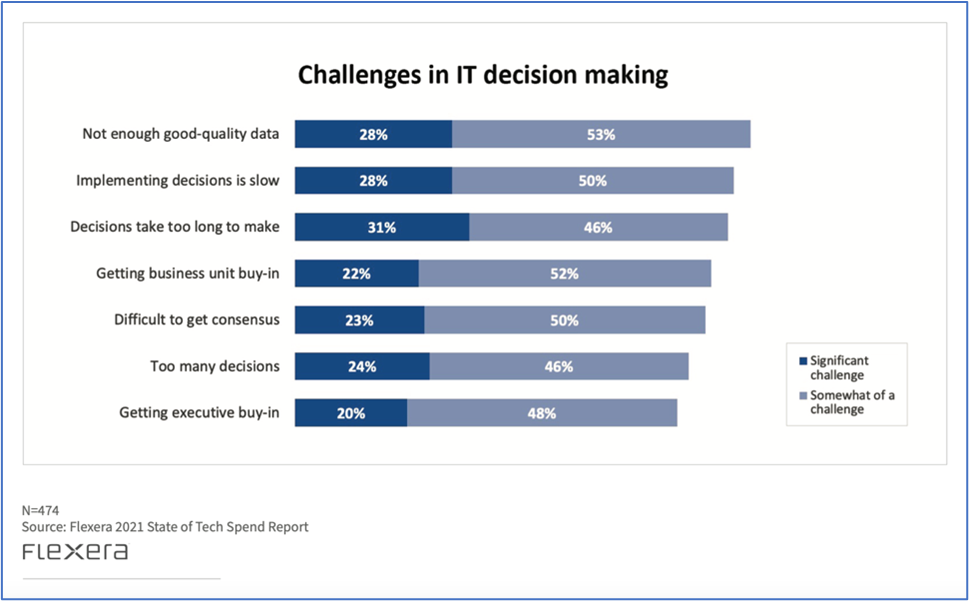
The top challenge in IT decision making is “not enough good-quality data,” cited as either somewhat of a challenge or a significant challenge by more than 4 out of 5 (81%) of survey respondents. The lack of this data slows the processes of making and implementing decisions related to vulnerability management.
Integrating IT asset inventory data into vulnerability and application rationalization efforts is a crucial part of mitigating risk in an organization and prioritizing strategic initiatives. You can’t make decisions about what to protect if you don’t have visibility into your assets.
3. Rely on threat intelligence.
Rather than reacting when an exploit hits the news or something noteworthy suddenly appears as a critical event in need of attention, it’s important that IT operations establish a regular process for detecting, prioritizing, and remediating vulnerabilities as they are disclosed.
Two common approaches leave the majority of disclosed vulnerabilities unaddressed:
- The most common way to prioritize patch activity is by prioritizing based on criticality score or Common Vulnerability Scoring System (CVSS) score, which ranges from 1 to 10. But this often doesn’t provide the best data on which to define remediation initiatives. Focusing on vulnerabilities with a CVSS score of 7 or more (which is a widely adopted best practice) only addresses about 50% of those vulnerabilities that are exploited. Most exploits actually have a “medium” CVSS score, between 4 and 7.
- When companies don’t have good visibility into what vulnerabilities require their attention, they typically focus on well-known applications (including Adobe, Google, Java, Microsoft, and Mozilla). Focusing on vulnerabilities for the top 20 vendors, however, only addresses about 20% of exploits.
Today, threat intelligence is now widely preferred, as it offers a more impactful metric for security and IT teams to prioritization of remediation efforts. By relying on threat intelligence—which verifies, normalizes, and scores each vulnerability—you can focus on vulnerabilities that are actually being exploited in the wild. A consistent, methodical, repeatable process means that any critical vulnerability (or a vulnerability with a high likelihood of exploitation) can be addressed as a matter of routine. This allows you to allocate time and resources to patching the vulnerabilities that have evidence of exploitation and that pose the most critical risk to your environment. By prioritizing vulnerabilities effectively, you may drastically decrease risks while only patching 10–20% of those applications in need of remediation.
With sufficient visibility into the assets that exist in your environment—and the vulnerability and threat intelligence to identify what’s vulnerable and its associated risk—an organization can greatly reduce its security risk.
Contributed by Bob Kelly (@rwk), director of product management at Flexera








