Nvidia has admitted that employee and internal data was stolen in an apparent ransomware attack last week.
The chip behemoth initially gave little away, announcing only that its “business and commercial activities continue uninterrupted” while the attack was investigated.
A new statement provided more information:
“Shortly after discovering the incident, we further hardened our network, engaged cybersecurity incident response experts, and notified law enforcement. We have no evidence of ransomware being deployed on the Nvidia environment or that this is related to the Russia-Ukraine conflict. However, we are aware that the threat actor took employee credentials and some Nvidia proprietary information from our systems and has begun leaking it online.”
Lapsus ransomware gang is believed to be responsible, with the group claiming that it has 1TB of Nvidia information in its possession.
Twitter screenshots suggest that the group claims to have “complete silicon, graphics and computer chipset files for all recent Nvidia GPUs,” and threatened to release information regarding the organisation’s Lite Hash Rate technology (LHR).
Delving deeper into the situation, threat intelligence analysts at Searchlight Security provided the following:
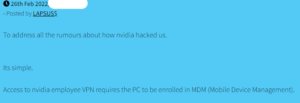
“If LAPSUS$ are to be believed, Nvidia’s systems were compromised via an employee’s VPN (Figure 1).
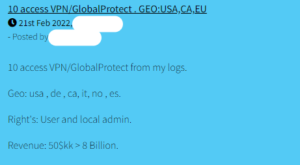
“Many dark web forums host auctions selling both user and administrator access to corporate VPNs. Sellers will variously specify the target company’s location, yearly revenue and size, industry or sector, brand of VPN being used and access rights available (Figures 2-3).

“Better dark web monitoring would enable companies to plug in their specifications in these categories and review a real-time feed of cybercriminal chatter relevant to their organisation, allowing them to assess their risk and adjust procedures accordingly. In addition, monitoring threat groups’ forum posts and messaging app chats builds a clearer picture of their modus operandi; LAPSUS$, for example, have shown a tendency to “tease” their attacks several days prior to their official announcement (Figures 4-5).
Learning the habits of these malicious actors can help businesses prevent and respond to cyberattacks as efficiently as possible, protecting valuable assets such as intellectual property from falling into the wrong hands (Figure 6).”

Ioannis Fragkoulopoulos, Customer Security and Professional services Director at Obrela commented on the incident, advising customers to “update their account log-in details, and not just for those accounts.” He added that “attackers could use the already leaked information to gain access to a number of user accounts to steal more information or launch larger attacks targeted at company networks. Organisations as a whole must practice cyber-resilience and take steps to mitigate the risks cyberattacks pose, before they actually happen. Cyberattacks are here to stay, so the only defence today is getting into a post-breach mindset before they happen to limit the negative outcomes. While there can be no denying that data breaches are commonplace today, you would hope a company as large as this would learn from previous incidents to harden its systems and improve security.”








