By Josh Horwitz, COO Enzoic
The biometric market is expected to soar to nearly $33 billion by 2022 as the technology is heralded as a bulletproof solution to thwart hackers. Consumers view biometrics favorably as it’s an easy way to log into their accounts, which is helping accelerate its widespread adoption. However, there are inherent risks that should be highlighted. Unlike passwords and other authentication methods, biometrics are static, are not deterministic, are public-facing and to top it off, not all users have biometric capable devices
Think about it; you can’t change your fingerprint or your face. If biometric information is exposed, then any account where you use this method of authentication is at risk, and there is no way to reverse the damage.
One recent example of a breach that exposed biometric information is Biostar 2, where the database was found unprotected and unencrypted. As a result, hackers could now have access to people’s fingerprints and facial patterns assuming this information was sold or traded on the dark web.
Another challenge with biometrics is that currently, not all devices have biometric capabilities. According to Pew Research, while 96% of Americans use a mobile phone, but roughly 19% of them do not use a smartphone. Additionally, nearly 74% of U.S. adults own a desktop or laptop computer, but many of those devices are older devices and do not include biometric readers. While we expect biometric capabilities to be incorporated into more devices in the future, it is not a feature that everyone can adopt today. As a result, organizations need to offer other authentication options in addition to biometrics.
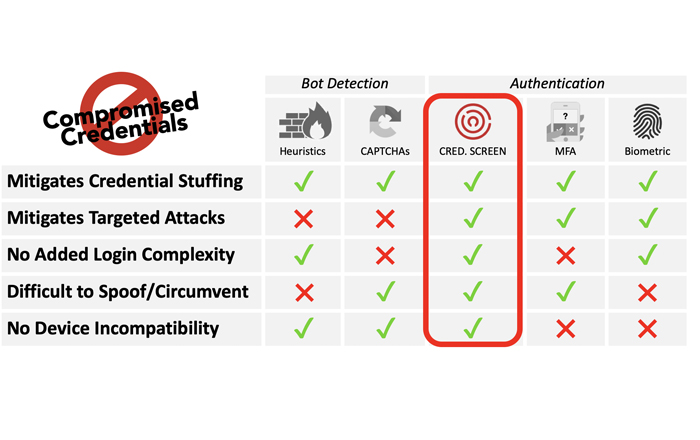
Some cybersecurity frameworks have concerns about biometrics as a stand-alone authentication method as well. According to NIST, the biometric False Match Rate (FMR) does not provide confidence in the authentication of the subscriber in isolation and it does not account for spoofing attacks. Biometrics are also probabilistic, whereas the other authentication factors are deterministic, like passwords. This means that biometrics control access with the probability of a match rather than a 100% match. Furthermore, biometric characteristics are not secret so, they can be spoofed. Facial information can be obtained online or through a photo of someone. With the rise of deep-fake technology, this will become even easier to spoof. Fingerprints can be lifted easily from objects like a coffee cup that someone touches at the office or public locations. Since they are public-facing and not changeable, this presents a significant security risk.
As with other types of authentication, once a cybercriminal gains access, they can then change the logins for these accounts and lock the legitimate user out of their account. This puts the onus on users, as well as the company, to take immediate action to mitigate the risk. If there is a breach, then users should immediately turn off biometrics on their devices and revert back to the default, which is still usually passwords or passcodes.
Relying solely on biometric authentication is a high-risk authentication strategy for all parties. Organizations should not be afraid to utilize biometrics as part of their identity management security strategy, but they also need to layer in other security elements to mitigate the potential risk.
Additionally, organizations should treat biometric data the same as traditional user credentials and passwords. This means that the biometric data should not be stored in plain text and a strong hashing algorithm should be utilized to make it as difficult as possible for hackers to crack the algorithm in the case there is a breach.
So, what other steps should organizations embrace in addition to biometrics?
Biometrics as a second factor of authentication: NIST 800-63b recommends that biometrics can be part of multi-factor authentication (MFA) rather than being the sole way to access accounts. The first factor can be login with credential screening running in the background, the second step can be a second-factor biometric confirmation instead of typing in a code or some other manual work required from the user. Combining the two low-user-friction methods of credential screening plus biometric-based MFA creates two layers of security while maintaining optimal user experience.
Adaptive authentication: This is a way that two-factor authentication can be configured and deployed. These systems cross-reference IP address, geolocation, device reputation, and other behaviors to assign a risk score to an inbound login session and step-up authentication factors accordingly. To increase effectiveness, they tend to be aggressive, often adding additional authentication factors that can increase customer frustration and abandonment. As a result, adaptive authentication should be used judiciously.
Screen for exposed credentials: Deploy a credential screening tool that compares customer credentials (user name and passwords combinations), against a database containing billions of compromised records. The tool must run continually in the background to ensure that compromised credentials or passwords are not in use.
Password-based authentication: If the biometric fails or is breached, it should default back to password-based authentication. However, best practice for password security must be followed to ensure passwords are not compromised or easily guessable.
Store Passwords Securely: Storing passwords or biometric data in plaintext is a major cybersecurity blunder. Hashing, where companies encode passwords and biometric data using a mathematical algorithm, is the answer to this problem. Organizations must ensure that their hashing strategy utilizes robust algorithms that make it almost impossible for hackers to reverse the hashing and read the data in plain text.
The simplicity and convenience of biometrics will ensure that its use continues to increase. However, due to the associated risks, organizations should selectively deploy it and ensure they have other layers of security in place in case of compromise or in case users do not have biometric readers. For example, in situations with a high-risk quotient such as banking or security clearance, biometric authentication is a great fit when paired with other security measures. Using biometrics for low-risk activities such as gaming or to access vending machines is an unnecessary risk.
Organizations should not be afraid to add biometrics to their security arsenal, but they must recognize that it’s not foolproof. To mitigate the risk, companies need to deploy a layered approach and utilize biometrics selectively as part of the overall identity management strategy. This will ensure that other fail-safes make it tough for bad actors to exploit the situation should there be a breach of biometric data.