New research has revealed that COVID-19 related phishing emails are still a serious threat as found by KnowBe4, a dedicated security awareness training and simulated phishing platform.
The results from the Q3 2020 top-clicked phishing report, exactly half of the most clicked phishing emails contained a coronavirus reference – and this was the most popular out of all the ones tested in the KnowBe4 phishing simulator. This was closely followed by social media messages (47%) which are commonly associated with phishing campaigns. LinkedIn dominated as the top social media email subject to watch out for.

The organisation also reviewed ‘in-the-wild’ email subject lines that show actual emails users received and reported to their IT departments as suspicious. The results are below.
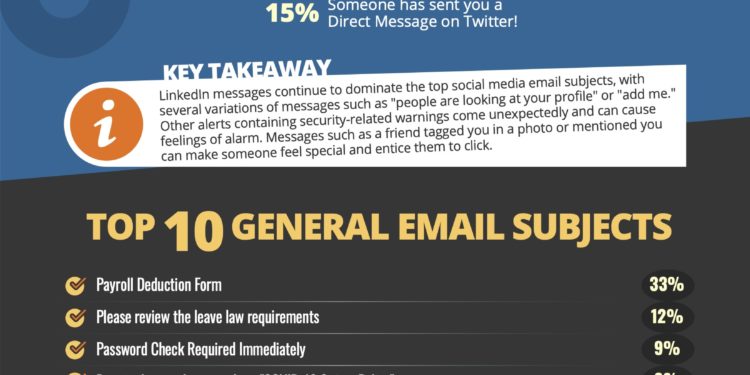
Top 10 General Email Subjects
- Payroll Deduction Form
- Please review the leave law requirements
- Password Check Required Immediately
- Required to read or complete: “COVID-19 Safety Policy”
- COVID-19 Remote Work Policy Update
- Vacation Policy Update
- Scheduled Server Maintenance — No Internet Access
- Your team shared “COVID 19 Amendment and Emergency leave pay policy” with you via OneDrive
- Official Quarantine Notice
- COVID-19: Return To Work Guidelines and Requirements
*Capitalisation and spelling are as they were in the phishing test subject line.
**Email subject lines are a combination of both simulated phishing templates created by KnowBe4 for clients, and custom tests designed by KnowBe4 customers.
“During this pandemic, we’ve seen malicious hackers preying on users’ biggest weak points by sending messages that instill fear, uncertainty and doubt,” said Stu Sjouwerman, CEO, KnowBe4. “Our Q3 report confirms that coronavirus-related subject lines have remained their most promising attack type, as pandemic conditions weaken judgment, and lead to potentially detrimental clicks.”
When investigating ‘in-the-wild’ email subject lines, KnowBe4 found the most common throughout Q3 2020 included:
- Microsoft: View your Microsoft 365 Business Basic invoice
- HR: Pandemic Policy Update
- IT: Remote Access Infrastructure
- Facebook: Account Warning
- Check your passport expiration date
- TeleMed Appointment Reminder
- Twitter: Confirm your identity
- Apple: Take part in our iPhone 12 trial and enter for the chance to win a FREE iPhone12
- Exchange ActiveSync service disabled for [[email]]
- HR: Benefit Report
*Capitalisation and spelling are as they were in the phishing test subject line.
**In-the-wild email subject lines represent actual emails users received and reported to their IT departments as suspicious. They are not simulated phishing test emails.