Rockstar Games, the publishers behind the popular Grand Theft Auto (GTA) franchise, announced earlier this week that data from the latest instalment of the GTA series has been leaked online.
The leak is being described as one of gaming’s biggest security breaches.
The publishers were unable to clarify how the “network intrusion” happened, but confirmed that “early development footage” from GTA VI had been stolen.
A user called teapotuberhacker posted the footage onto the GTAForums site.
The hacker claimed to have gained access to the data by breaching Rockstar’s internal feed on the Slack messaging app. They then invited executives to negotiate to avoid further leaks.
It has been reported that the ransom data could include source code, testing builds, and assets. All of these could be damaging to the company’s operations if released.
Rockstar are trying to get social media posts that contain the leaked information taken down. The original forum posts have been taken down by moderators.
On Monday, the company said it was “extremely disappointed to have any details of our next game shared with you all in this way”.
“Our work on the next Grand Theft Auto game will continue as planned and we remain as committed as ever to delivering an experience to you, our players, that truly exceeds your expectations,” it added.
But what do the experts think?
Chris Hauk, Consumer Privacy Advocate at Pixel Privacy
“Attacks like the Uber and Rockstar attacks emphasize the need for organizations to increase their security measures, keep systems updated, and harden their systems against an attack before it happens. However, it is a game of chess, where each side is forced to react to unexpected moves by the other side, scrambling to plug security holes only after they are exploited.”
Paul Bischoff, Consumer Privacy Advocate at Comparitech
“Although the leaked video is what’s making headlines, an hour of gameplay footage isn’t going to affect much outside of Rockstar’s marketing efforts. Perhaps more concerning is the stolen source code, which could allow attackers to craft cheats and exploits, or for players to compile and play the game before it’s released. Although the attacker claims to have stolen source code, they have not leaked it yet (as of time of writing).”
Satya Gupta, CTO and founder at Virsec
The fact that an attacker from the group “Lapsus$” attacked Uber and also Rockstar is inconsequential. The substantive part is that they both got attacked.
As we know from the Uber Attack Kill Chain (screenshot below) the attacker overwhelmed a privileged employee to accept a two-factor authentication request that was triggered by the attacker. Once the attacker was able to infiltrate the Uber infrastructure, they moved laterally until they found the network shared drive and the domain controller. From there the attacker gained access to numerous apps and the underlying infrastructure before performing data exfiltration.
The lesson for big-tech is to make sure (a) to train employees (especially those with higher privileges) to be very careful when approving MFA requests and (b) to deploy runtime protection solutions that implement a positive security model and hence offer zero dwell time protection.
Martin Jartelius, CSO at Outpost24: Given that the gaming industry is now worth over $300 billion, it is a lucrative target for malicious cyber-attacks, and this most recent on Rockstar Games proves how disruptive an attack can be.
For instance, the leak has negatively impacted share prices of the company that owns Rockstar Games. Moreover, intellectual property will fetch for a good price on the dark web which can be used by potential competitors for their own gain or other hackers to cause more trouble.
Both the information that is leaked and the breach itself may have a direct impact on a company’s project delivery, with any potential delays adding to the overall costs. To avoid such scenarios going forward, organisations must ensure security best practises are being followed while monitoring for any adverse behaviour across systems
Markus Strauss, Head of Product Management at Runecast
“Having game footage leaked prior to a release is not uncommon and is allegedly often a common practice by development studios themselves. Given the official statement from Rockstar Games about the network intrusion, this does not seem the case here, however. Given the intrusion method and the potential connection to the Uber attack it is likely this attack again used existing vulnerabilities that the attacker was able to exploit to gain access to a network. One must wonder how much effort is spent on basic vulnerability assessment and patching in such cases.”
Erfan Shadabi, Cybersecurity Expert at comforte AG:
Given that 2013’s GTA 5 is considered one of the most successful video games of all time and there’s growing fan demand for the new instalment, it is no surprise that it became a target for hackers. What comes to mind when we think about security breaches is usually the stealing and selling of personal user or employee data, but this attack is slightly different. The hacker stole, through the Slack messaging platform, a lot of new gameplay related assets – which can be highly valuable on the dark web and/or highly sought after by fans on social media. When stolen data like this is published on social media it can be almost impossible to limit the damage and reach of the data.
Gaming organizations should take privacy on employee messaging platforms (where highly sought-after information is stored and exchanged) as seriously as they would user data privacy. This can be achieved by building into their data infrastructures more than just the bare minimum level of security and reviewing all service providers frequently. Their strategy should be data-centric, with an assumption that threat actors might try to get to this cache of information. When you protect the data itself, rather than the perimeters around it, with methods such as tokenization or format-preserving encryption, you obfuscate the sensitive parts and render it incomprehensible and useless to hackers. Better yet, data-centric security is not dependent on protected borders and travels with the data.
Louise Ferrett, Threat Intelligence Analyst at Searchlight Security:
“Users on cybercriminal and dark web forums are pointing to a member of LAPSUS$ as the perpetrator of the cyberattack against Rockstar that has led to the leak of the latest Grand Theft Auto game. For example, this post on DoxBin accuses the LAPSUS$ member known by the alias ‘White’ for being behind the attack and last week’s attack against Uber:
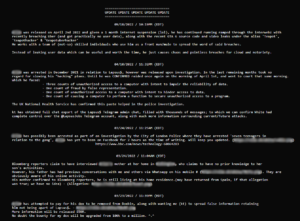
“As we can see from this screenshot, this is the latest in a series of updates that the user has provided since they originally doxxed (shared the identify of) White back in January:
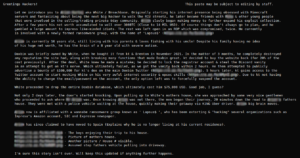
“It goes without saying that attributions on cybercriminal forums should not be taken as concrete proof, especially since this user clearly harbours a grudge against White. However, the attacks on Rockstar and Uber do fit the pattern of the LAPSUS$ group’s previous attacks, which focused on noteworthy targets and has previously included the gaming company EA, which means it is possible that the user on DoxBin is telling the truth.”








