There’s a lot of information and misinformation out there surrounding COVID-19, aka the Coronavirus.
It dawned on me that writing risks is literally one of the fundamental skills of an information / IT / Cyber security professional. So why not try to make sense of the whole pandemic by thinking of it like malware.
This involves a two-step process, first write out the risk in understandable terms, and secondly, create a usable and understandable risk matrix.
Step 1: Documenting the risk
I have previously posted a blog on writing better risk statements. The process involved structuring the message – for that I used the journalistic trope called the Inverted Pyramid. It structures information in a way that prioritises the facts from most to least important.
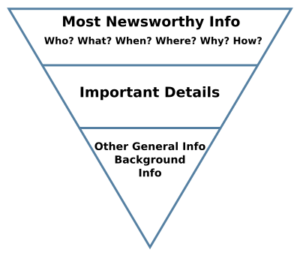
The headline
There is a new disease called Coronavirus, also known as COVID-19. It’s a viral disease that can affect the lungs and airways of systems (humans)
Adding Detail
This disease can impact breathing and heart. It is particularly potent against legacy systems (people over 70) and unpatched vulnerable systems (those with underlying health issues).
100% of systems (humans) have lungs and a heart and are affected in some form or another by viruses such as influenza and the common cold.
Contextualize
It is expected that 80% of the population will come into contact with the virus. For young and healthy systems (humans), the symptoms may be unnoticeable or mild, with only small performance degradation. However, they can pass on the virus to other vulnerable systems (humans).
Call to action
There is no vaccine or cure to COVID-19 at present. But measures should be taken to reduce the likelihood of catching and spreading the virus. These can be distilled into three actions
- Better hygiene: Washing hands frequently like your mother taught you, covering your mouth when sneezing or coughing.
- Social distancing: Something introverts are exceptionally good at and what many women wish more men were good at.
- Isolation: Netflix and chill, only by yourself. Sorry.
Step 2: The risk matrix
Now that we have the risk documented, we need a matrix to help visualize the risk. For this I turned to my long-time friend and former CISO Thom Langford, with whom I collaborated with previously to formulate the Malik-Langford risk model.
Taking that model, we put our heads together and updated it to the COVID-19 special risk model v3.0
Risk Management Model COVID-19

And there you have it, a risk statement and matrix to help you make sense of COVID-19. Hope you all stay safe and healthy. Look after each other!








