Ever since the second half of the 20th century when the first hackers were tinkering with computers in garages, there has been heated debates about what name should be attributed to the trade of computing security. In order to put an end to an argument that has plagued security professionals for well over half a century, we conducted a survey that was sent directly to over 5,000 industry professionals. Of the 5,000 experts surveyed, we received 570 responses. The purpose of the survey was simple: to reach a consensus as to what we should be calling our industry.
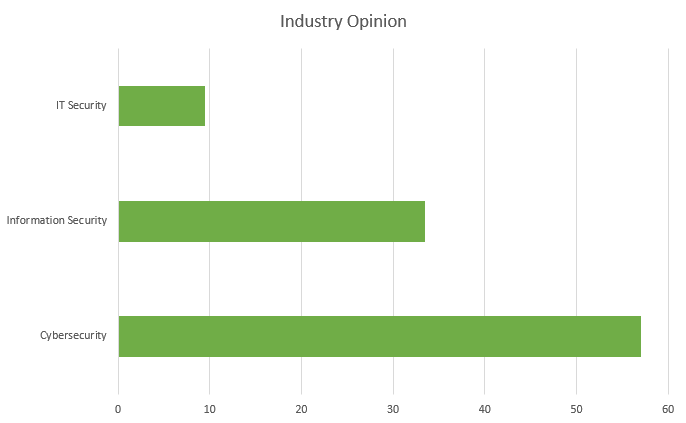
The survey consisted of the three most widely accepted definitions of the industry: ‘Cybersecurity’ (without a space, but that’s a discussion for another time), ‘IT Security’ and ‘Information Security’. The results were resounding. The vast majority (57%) voted in favour of ‘cybersecurity’ while only a third (33.5%) voted for ‘Information Security’. The least popular was ‘IT Security’ with only a 9.5% share. With these results in mind, I will henceforth use the term ‘cybersecurity’ when referencing the industry.
According to Shan Lee, CISO at TransferWise, the root of the debate stems deeper than finding the correct colloquialism. In fact, Lee proposed that there was a “generational” gap between definitions. Lee, who has more than two decades of experience securing networks, shared that he himself, along with many colleagues were “dragged kicking and screaming into the world of cyber”. While, one would be remis not to laugh at the ironically comical image of security professionals being dragged into the 21st century, their reticence to adopt a catch-all definition such as ‘cybersecurity’ is not unfounded, and can be traced to the fact that the industry itself is undergoing perpetual progression.
A major grievance with the word ‘cyber’ can be traced to media perception and portrayal. One must argue that to the average consumer, the word ‘cyber’ has far more exciting connotations than the rather banal definition of ‘Information Security’. In fact, the word cyber was originally penned by famed Sci-Fi writer William Gibson. Gibson coined the phrase ‘cyber’ because he “liked the way it felt in the mouth” going on the state that he “thought it sounded like it meant something while still being essentially hollow.” It is perhaps for this reason, and the excitement that was fuelled by a simple word, that the industry is widely referred to with the prefix ‘cyber’ in both media discourse and popular culture (with the noteworthy exception of the IT Security Guru). Likewise, the description of digital adversaries seems to be confirmed as ‘cybercriminals’, therefore it makes sense to conversely label our white-hat-wearing protagonists as ‘cybersecurity’ Experts.
As technology advances, so too does the job description of those tasked with securing business-critical information. As Oleksiy Gayda, a principle threat hunter, explained: “the introduction of operational technology (OT) and the ever-growing market of Internet of things (IoT) means that we’ve moved past just securing the information. We’re now also securing infrastructure, appliances, cars, medical devices, etc. I think of “Information Security” as the subset of cybersecurity, mostly owned by the “risk management” teams”. With this in mind it is clear to see why the usage cybersecurity has become so widespread. Indeed, many lead generation tools rank ‘cybersecurity’ as both the leading, and most relevant term to encapsulate the industry. Therefore, by labelling the industry as anything other than ‘cybersecurity’ we are potentially missing out on the possibility of lead generation and good coverage because of stubbornness not to conform to societal norms.
As the industry progresses, so too will the skills required to stay one step ahead of cybercriminals. So whatever title you choose to self-identify as, be it cybersecurity specialist, Information Security expert or IT Security professional, we are all fighting the same enemies. The war against cybercriminals will never rest so neither will we. Regardless of what you want to call yourself, we all have the same aim: winning the war against cybercriminals and protecting sensitive data. However, let’s face it; the word ‘cyber’ is pretty sexy…








