Supplier: Edgescan
Website: www.edgescan.com
Price: Based on assets
Scores
Performance 5/5
Features 5/5
Value for Money 4/5
Ease of Use 5/5
Overall 5/5
Verdict: Fullstack vulnerability management made easy – Edgescan does all the hard work so you don’t have to
The pandemic has undoubtedly led to a massive surge in cyber-attacks but even as restrictions start to ease, businesses can’t afford to relax as these threats will keep evolving and continue long into the future. Vulnerability assessment, management and mitigation are critical to survival in this harsh landscape but far too many businesses rely only on automated solutions which can leave gaping holes in their cyber defences.
One of the biggest problems with vulnerability assessment automation is assessment coverage and the number of inaccuracies, false positives and false negatives it can generate. Feeding these into a threat tracking system can be a complete waste of resources as security teams will spend valuable time chasing down false findings.
Edgescan takes an innovative approach to vulnerability assessment by combining machine-based analytics and automation with human intelligence. Coined ‘fullstack vulnerability intelligence’, Edgescan uses a two-fold approach allowing it to automate common, repetitive tasks but bring human decision making to more complex duties such as vulnerability validation, risk assessment and prioritization. It also covers both the web application layer and supporting host infrastructure.
Using dedicated teams of in-house security analysts combined with custom vulnerability automation, Edgescan sorts the wheat from the chaff and presents its findings to customers showing clearly where they should be directing their resources. It manually validates threat feeds ensuring only actionable data is being received allowing businesses to focus on the weaknesses and risks that matter.
Deployment
Easily deployed as a SaaS (security as a service) solution, Edgescan is completely agent-less and requires no on-premises scanners as everything is run from the cloud. Onboarding is equally pain-free as the customer fills in a form declaring the assets they want protected which can include network devices, applications, APIs and anything with an IP address or URL that could be exposed.
If internal network scanning is required, Edgescan deploys a production ready jump–box as a virtual machine (VM) that provides a secure connection to the customer network. An Amazon Machine Image (AMI) version is also available on AWS allowing Edgescan to assess a company’s cloud services.
Licensing options are extensive with Edgescan Essentials providing the tools for foundational assessments across an enterprise network to discover and determine a basic web app security posture. The Standard license expands services to include authenticated testing, the Advanced license adds on-demand logic and penetration testing for critical apps while the Host version provides vulnerability management services for hosts and servers.
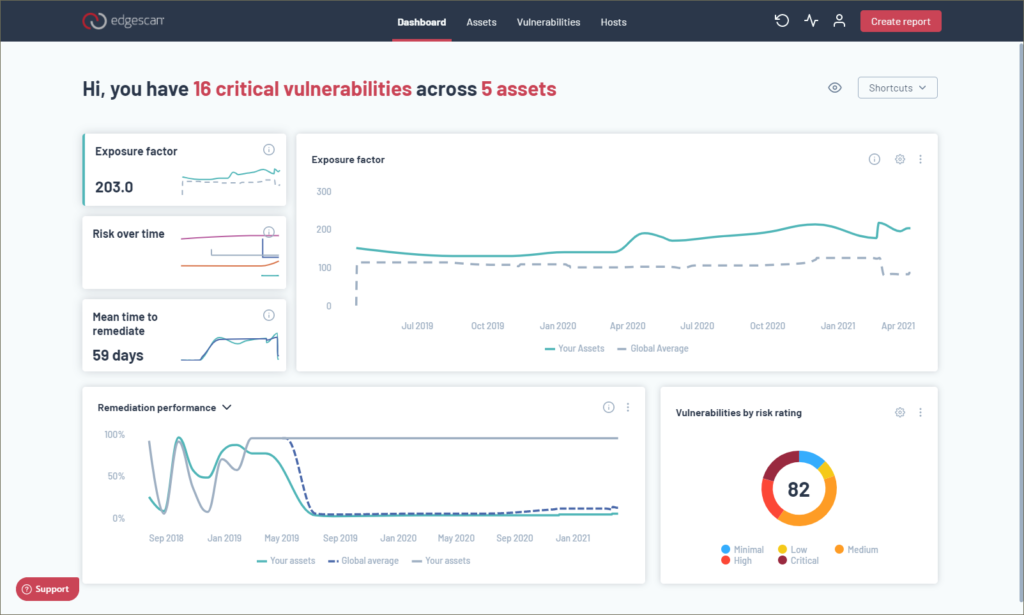
The new web console
Having previous experience with Edgescan, we can safely say its new award-winning (Good Design Awards 2020) user interface is a significant improvement. The original dashboard was very informative but the revamped web interface places all the most important information at your fingertips and provides improved user navigation.
The new dashboard presents a simplified actionable data view that shows clearly what your security posture is. The score presented by the exposure factor graph is derived by taking the combined vulnerability score for all your public facing assets and dividing it by the number of exposed assets.
The risk over time graph is self-explanatory while the MTTR (mean time to remediate) graph shows how effective your teams are at closing vulnerabilities. Select any of these graphs and the main window to the right changes to reflect their values where you can apply filters to show all or specific assets over a custom time period.
The lower graph can be changed to show a range of valuable information such as the CVSS landscape, average patch performance for assets with CVE-related vulnerabilities, the top assets at risk and your score for remediation performance. The pie chart alongside can be set to show the top vulnerabilities grouped by threat, severity or risk and clicking on the chart transports you straight to the console’s vulnerabilities page with a filter already applied that is based on the section of the chart selected.
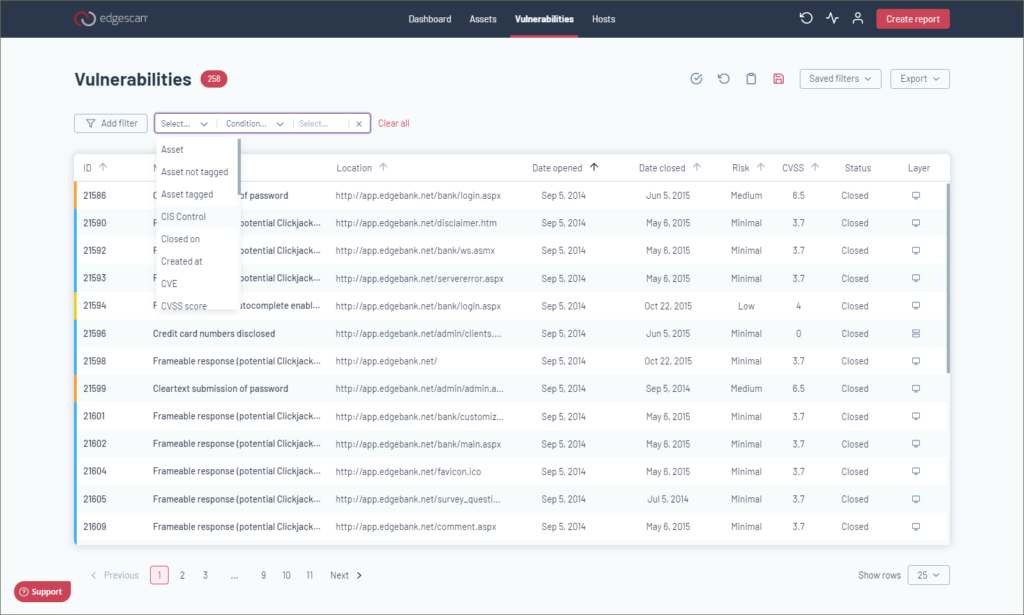
Assets, vulnerabilities and hosts
Many of the menus from the previous console have been tidied up and are now accessed from a simple navigation bar across the top with four options for viewing the dashboard, assets, vulnerabilities and hosts. You can see all your assets in one screen and apply a wide range of filters to fine-tune the information presented. Custom filters can be saved and easily recalled at the click of a link and everything in the GUI can also be accessed via the Edgescan API if required.
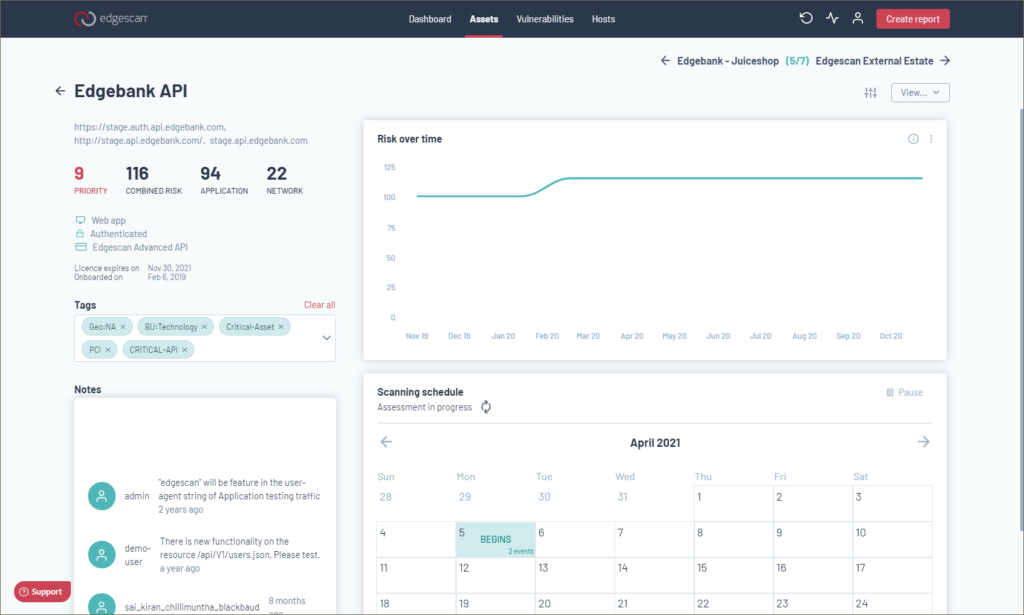
Click on an asset and it takes you to a deep-dive screen which reveals a wealth of information such as its priority, combined risk score, associated applications and networks, risk over time and a scanning schedule.
The view menu above the risk graph shows how smart Edgescan is as it’ll transport you directly to the relevant screen based on your selection. Choose the highest risk vulnerability view, for example, and with one click, the screen changes to show a critical listing for the selected asset.
APIs
API security assessment is a key strength of Edgescan as it builds out from external IP monitoring to pinpoint hosts that have APIs on them. It also handles APIs differently to other security vendors that treat them as no different to web apps and run the same tests on them all which rarely provide any useful information on API vulnerabilities.
Web apps are designed to interact with humans whereas APIs interact with machines so Edgescan runs different sets of tests on them. Using automated multi-layered checks and human verification, it probes endpoints to discover all known, unknown and shadow APIs, sends requests to see if and how they respond and determines their security posture.
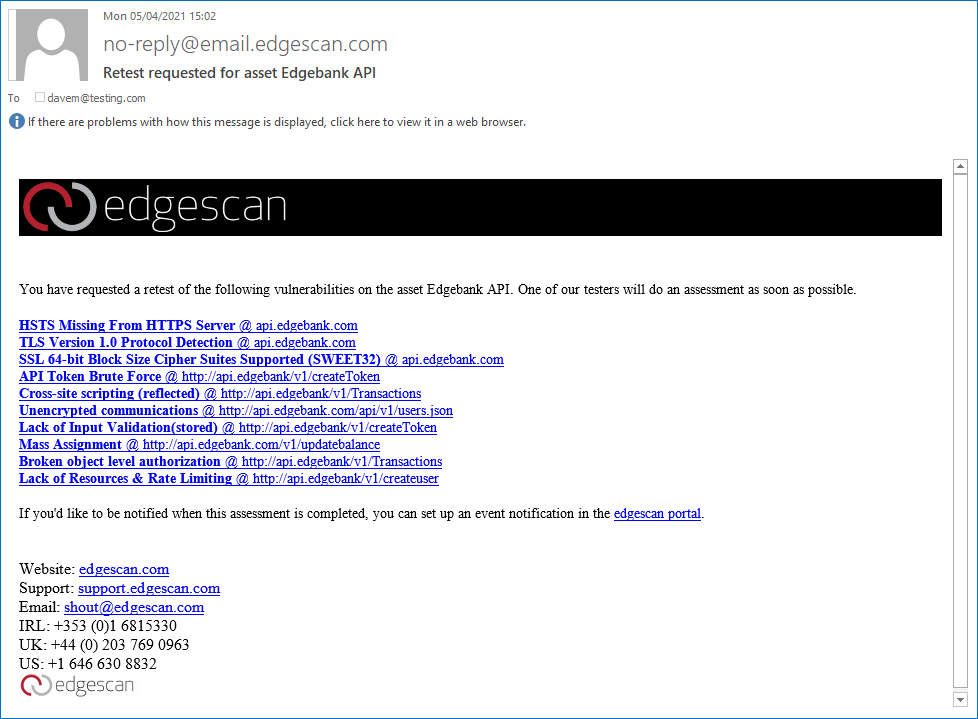
You can view all API information in the console’s asset view and drill down into each one for more information. The resultant screen shows details such as the API’s priority, combined risk score plus affected applications and, unlike other solutions that charge per scan, the licenses allow you to submit retest requests to Edgescan’s security experts.
Conclusion
By delivering a smart combination of scan automation and human intelligence, Edgescan takes vulnerability assessment and management to the next level. Its security experts manually validate all feeds so customers can be assured accurate vulnerability data which can result in a massive time saving for any organisation.
Edgescan clearly shows all detected vulnerabilities accompanied by valuable advice on fixing them but if a customer has any issues understanding the threat, Edgescan support can guide them through the remediation process. It’s simple to deploy with flexible licensing schemes, the new web console is very well designed and Edgescan’s security teams make false positives a thing of the past.








